Question 6 of 49
Alice, a Server Administrator (Tomcat), wants to ensure that Tomcat can be shut down only by the user who owns the Tomcat process. Select the appropriate setting of the CATALINA_HOME/conf in server.xml that will enable him to do so.
Correct Answer: C
Question 7 of 49
Which of the following method will help you check if DEBUG level is enabled?
Correct Answer: A
Question 8 of 49
Which of the following elements in web.xml file ensures that cookies will be transmitted over an encrypted channel?
Correct Answer: D
Question 9 of 49
In which phase of secure development lifecycle the threat modeling is performed?
Correct Answer: D
Question 10 of 49
Identify the type of attack depicted in the figure below:
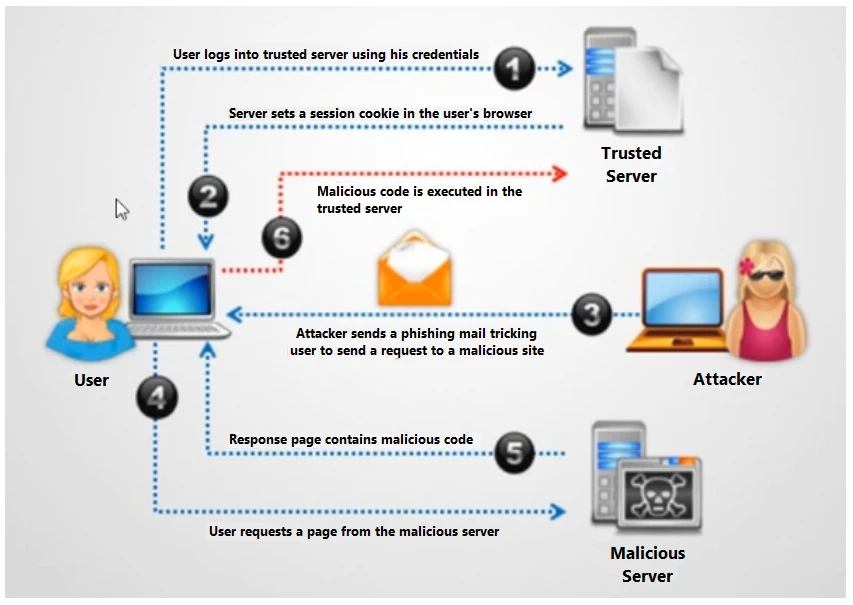

Correct Answer: B