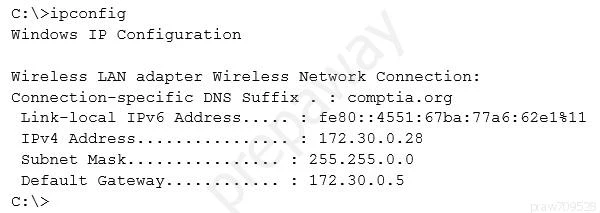
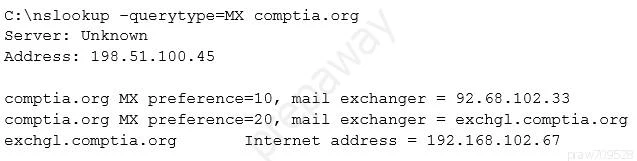
The suggested answer is A.
An ISA (Interconnection Security Agreement) is a document that outlines the technical and security requirements for establishing, operating, and maintaining a secure connection between networks or systems belonging to different organizations. In the context of setting up a business-to-business VPN, this agreement would detail the security measures, protocols, and rules that both parties must adhere to, ensuring the integrity, confidentiality, and availability of the data being transmitted over the VPN.