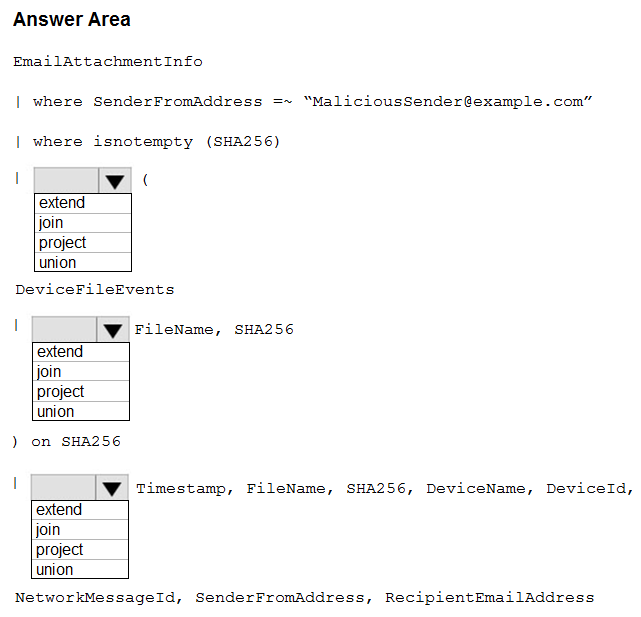
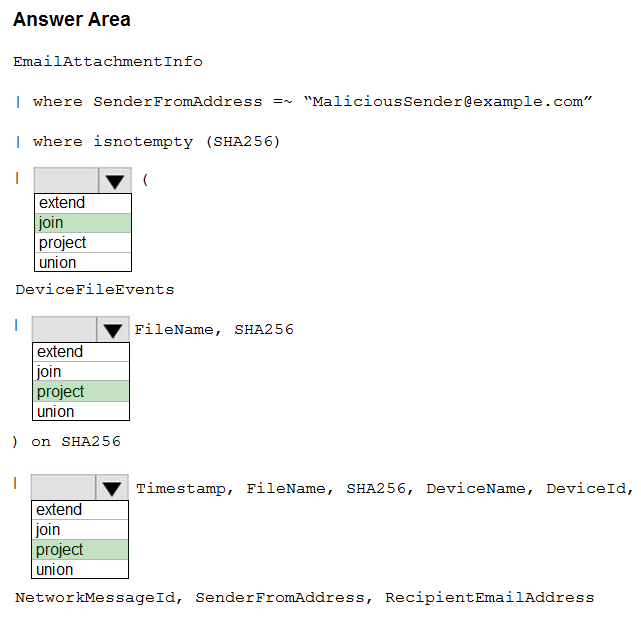
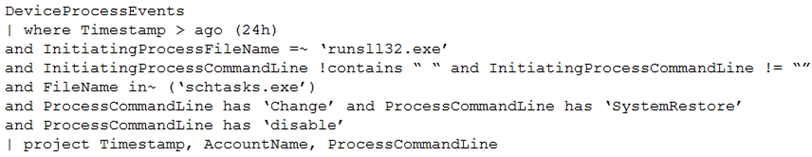
DRAG DROP -
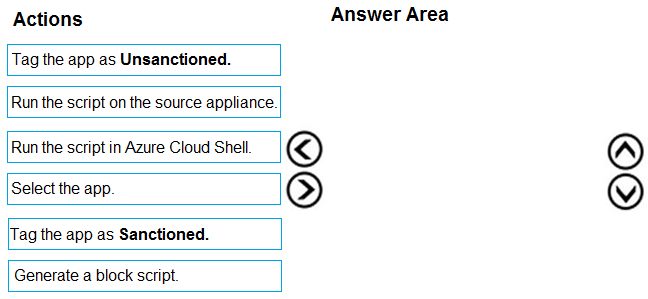
You open the Cloud App Security portal as shown in the following exhibit.
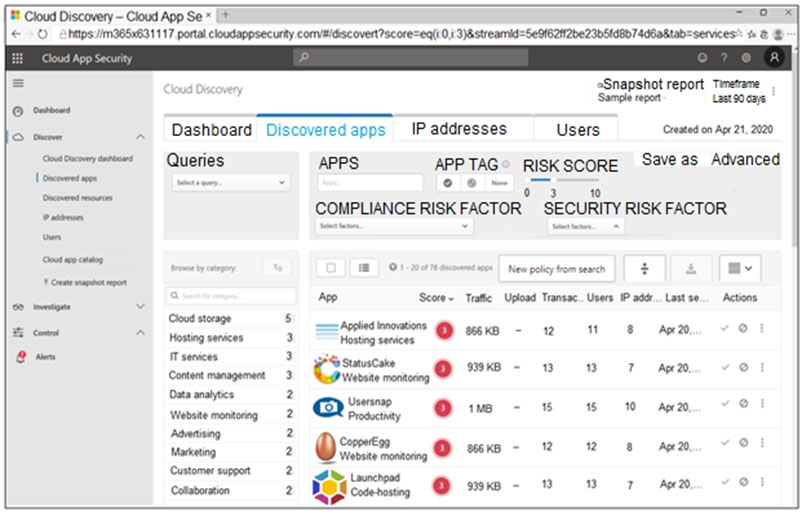
Your environment does NOT have Microsoft Defender for Endpoint enabled.
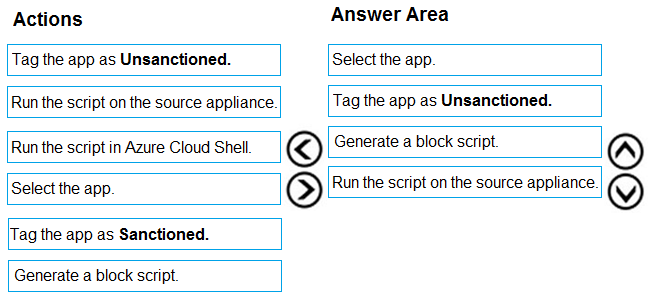
You need to remediate the risk for the Launchpad app.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place: