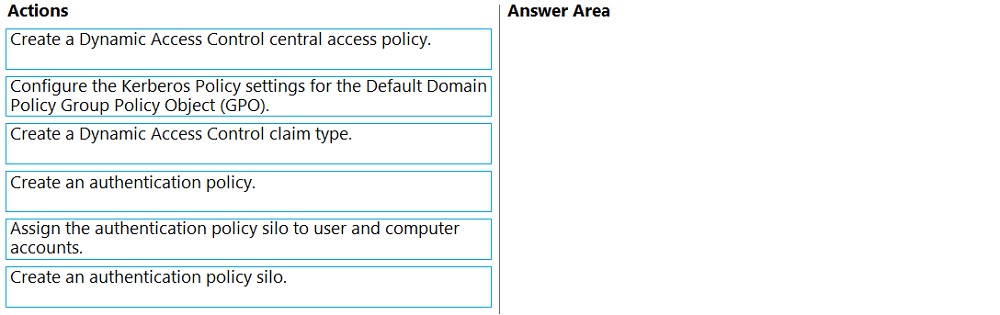
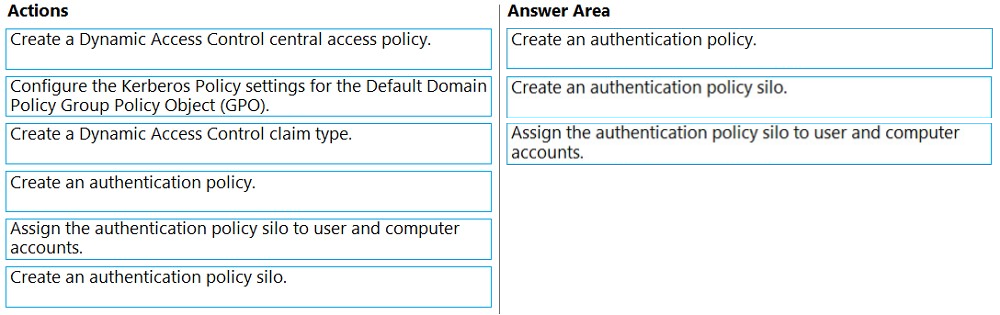
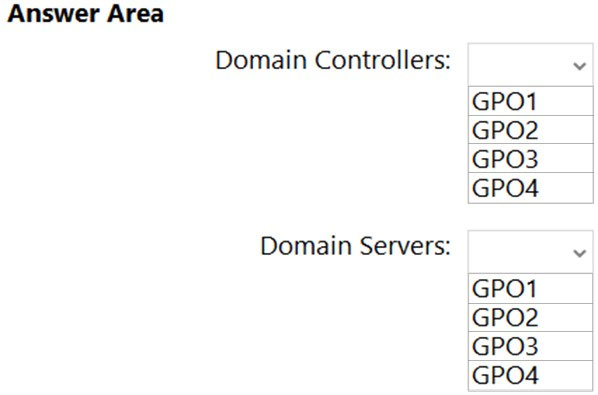
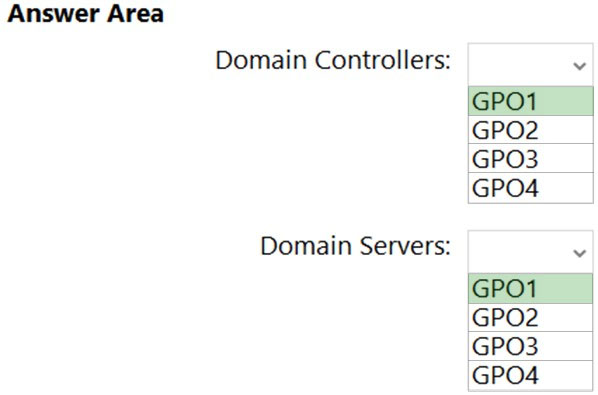
DRAG DROP -
Your network contains an Active Directory Domain Services (AD DS) domain.
You need to implement a solution that meets the following requirements:
✑ Ensures that the members of the Domain Admins group are allowed to sign in only to domain controllers
✑ Ensures that the lifetime of Kerberos Ticket Granting Ticket (TGT) for the members of the Domain Admins group is limited to one hour
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place: