Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
You work for a company named Contoso, Ltd.
The network contains an Active Directory forest named contoso.com. A forest trust exists between contoso.com and an Active Directory forest named adatum.com.
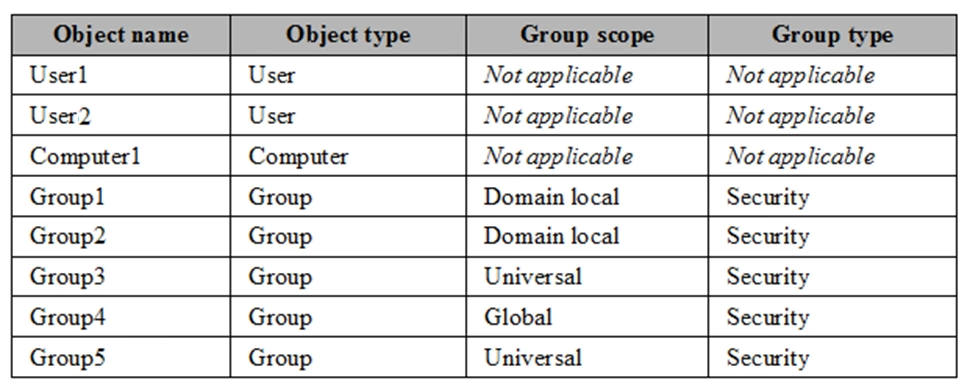
The contoso.com forest contains the objects configured as shown in the following table.
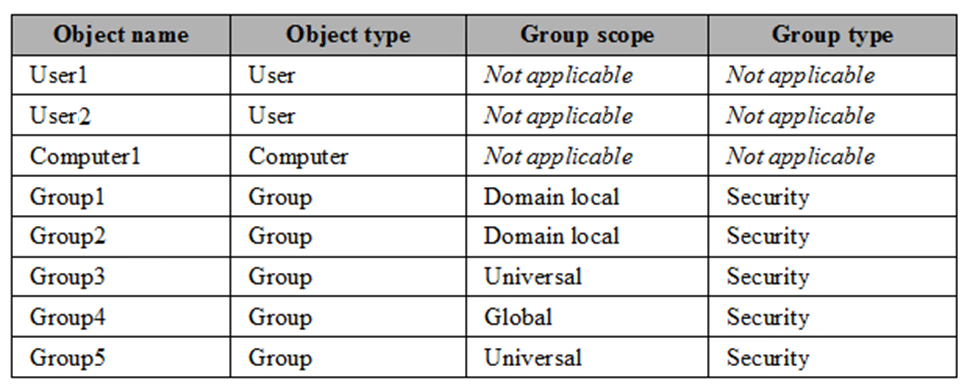
Group1 and Group2 contain only user accounts.
Contoso hires a new remote user named User3. User3 will work from home and will use a computer named Computer3 that runs Windows 10. Computer3 is currently in a workgroup.
An administrator named Admin1 is a member of the Domain Admins group in the contoso.com domain.
From Active Directory Users and Computers, you create an organizational unit (OU) named OU1 in the contoso.com domain, and then you create a contact named Contact1 in OU1.
An administrator of the adatum.com domain runs the Set-ADUser cmdlet to configure a user named User1 to have a user logon name of User1@litwareinc.com.
End or repeated scenario.
You need to ensure that Admin1 can add Group2 as a member of Group3.
What should you modify?