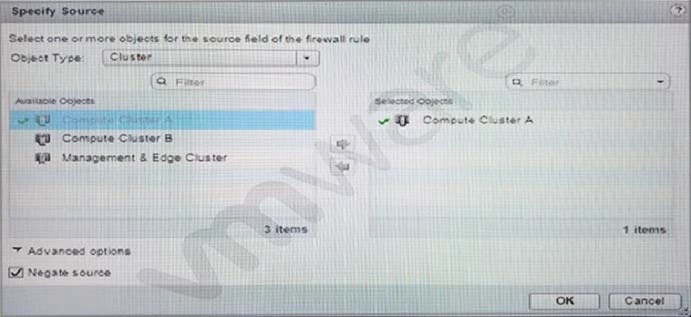
The suggested answer is B.
If Negate Source is selected, the rule is applied to traffic coming from all sources except for the source identified under the object type. This means that the specified source is excluded from the rule. If Negate Source is not selected, the rule is applied to traffic coming from the specified source. Therefore, selecting Negate Source effectively inverts the selection criteria for the specified source.