A vSphere administrator is working in a high security environment. The administrator wants to ensure unencrypted VMs can be migrated securely.
What should the vSphere administrator use to meet this requirement?
A vSphere administrator is working in a high security environment. The administrator wants to ensure unencrypted VMs can be migrated securely.
What should the vSphere administrator use to meet this requirement?
To ensure that unencrypted virtual machines (VMs) can be migrated securely in a high-security environment, the vSphere administrator should use encrypted vSphere vMotion. Encrypted vSphere vMotion ensures that the data transferred during the migration process is encrypted, protecting it from unauthorized access or interception. This method directly addresses the requirement of secure migration for unencrypted VMs.
Which two tasks are allowed in the X-Lence data center? (Choose two.)
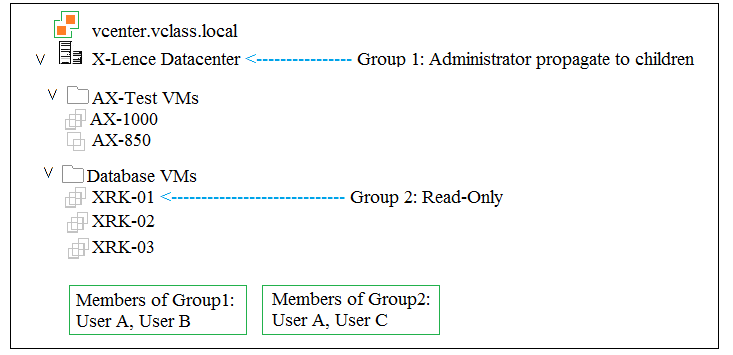
In the given context, Group 1 has Administrator privileges with propagation to children, meaning full access to tasks such as deleting VMs. Group 2 has Read-Only privileges, which limits tasks to viewing only. User B from Group 1 can delete XRK-01, and User A from Group 1 can take snapshots of AX-1000. Therefore, the two tasks allowed are User B deleting XRK-01 and User A taking a snapshot on AX-1000.
What are two components of a VM-Host affinity rule? (Choose two.)
Two components of a VM-Host affinity rule are Host Group and VM Group. A Host Group specifies a set of hosts to which virtual machines should or should not be assigned according to the rule, while a VM Group specifies the set of virtual machines that are subject to this rule. These selections align with the operational requirements for enforcing VM-Host affinity rules.
What does ESXi Autoconfiguration do?
ESXi Autoconfiguration primarily configures the system network and storage devices. This process ensures that the ESXi host is properly set up with the necessary network and storage configurations to operate effectively in the virtualized environment.
An administrator is using vSphere Web Client to configure the firewall to allow specific third-party application SSH access to an ESXi Host.
What is the most secure way to configure the firewall rule?
The most secure way to configure the firewall rule is to specify the remote IP subnet range in the IP List. This ensures that only the specified IP addresses can access the ESXi host via SSH, limiting potential security risks by preventing unauthorized access from arbitrary IP addresses. Allowing connections from any IP address or disabling the firewall would significantly compromise security, and enabling lockdown mode does not address the configuration of specific firewall rules.