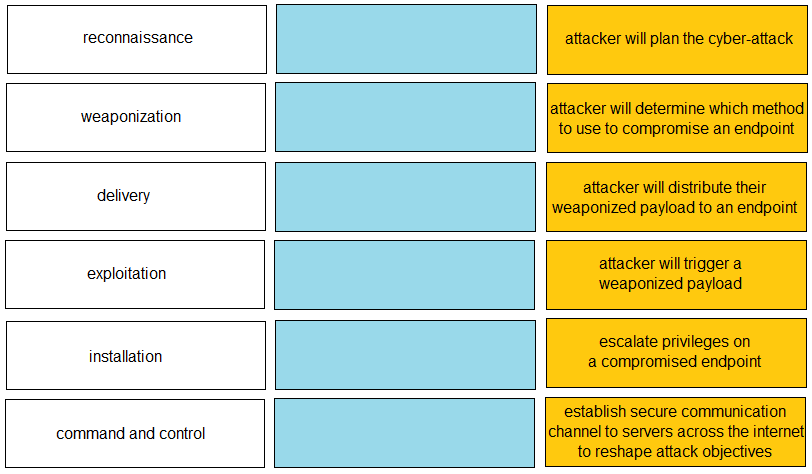
DRAG DROP -
Given the graphic, match each stage of the cyber-attack lifecycle to its description.

Select and Place:
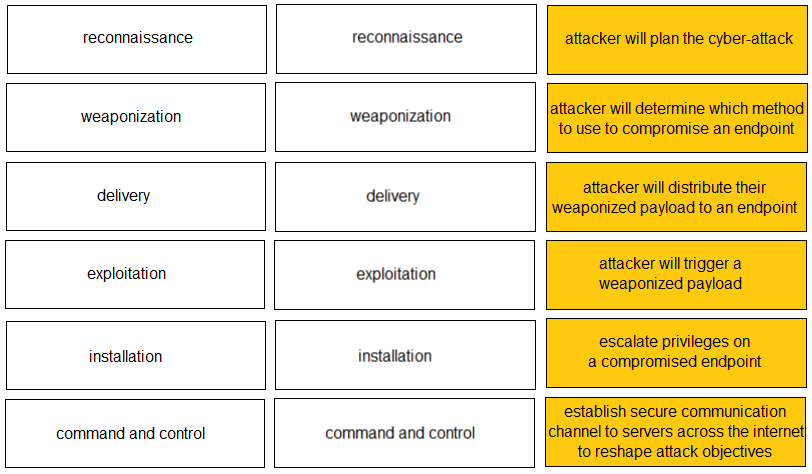
DRAG DROP -
Given the graphic, match each stage of the cyber-attack lifecycle to its description.

Select and Place:

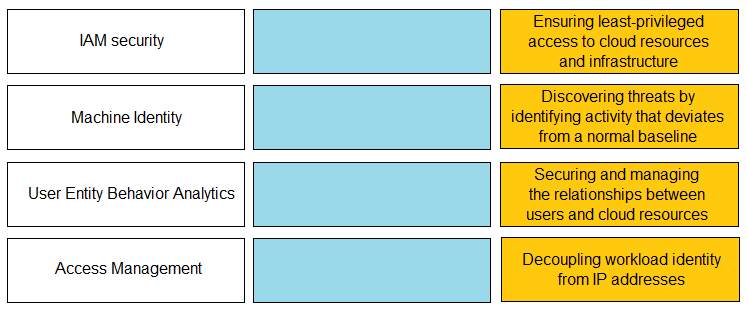
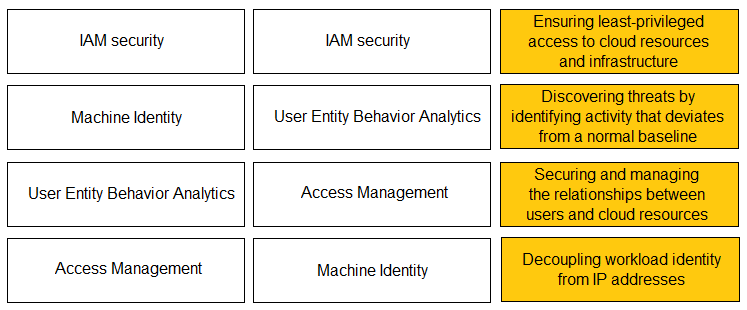
DRAG DROP -
Match the Identity and Access Management (IAM) security control with the appropriate definition.
Select and Place:
On an endpoint, which method should you use to secure applications against exploits?
To secure applications against exploits on an endpoint, the most effective method is to apply software patches. These fixes address vulnerabilities in applications, operating systems, and firmware, reducing the risk of exploitation by malicious actors. This approach ensures that known security holes are sealed, keeping the systems protected against various types of attacks.
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
AutoFocus by Palo Alto Networks is designed to enable a proactive, prevention-based approach to network automation that accelerates security analysis. It provides threat intelligence directly accessible within the Palo Alto Networks platform, aiding security professionals by speeding up existing workflows and allowing for in-depth investigation into suspicious activity. This automation helps in enhancing the security posture without requiring additional specialized resources.
Which endpoint product from Palo Alto Networks can help with SOC visibility?
Cortex XDR is Palo Alto Networks' endpoint product designed to enhance SOC (Security Operations Center) visibility. It helps detect and respond to threats by providing visibility across endpoint, network, and cloud data, applying analytics, and automating response actions.