Which THREE are valid Oracle Cloud Infrastructure (OCI) options for connecting and routing between the two VCNs? (Choose three.)
To enable routing between two Virtual Cloud Networks (VCNs) in the same region but different compartments, the following are valid Oracle Cloud Infrastructure (OCI) options: Create two Dynamic Routing Gateways (DRGs), attach one VCN to each DRG, and establish Remote Peering Connections (RPC) between the DRGs, then add appropriate routes in the VCNs' route tables. Another method is adding a Local Peering Gateway (LPG) to each VCN, establishing a peering connection between the LPGs, and configuring the routes accordingly in the VCNs' route tables. A third option is to create a single Dynamic Routing Gateway (DRG), attach both VCNs to the DRG, and add routes in the VCN route tables using the DRG as the next hop for the CIDR prefixes of the other VCN. These solutions ensure proper routing and connectivity between the VCNs without requiring FastConnect.
How can you deploy a load balanced application to your OCI Container Engine for Kubernetes (OKE) cluster using these images?
To deploy a load balanced application to your OCI Container Engine for Kubernetes (OKE) cluster using the containerized images, you need to follow a few key steps. First, you must create a named secret, which allows the Kubernetes cluster to pull the images securely from the OCI Registry (OCIR). Then, you add this secret to the manifest file alongside the location of the docker image. Additionally, you need to include a service of type LoadBalancer in the manifest file to ensure the application is accessible externally via a load balancer. Finally, deploy the manifest file. This process ensures secure and balanced deployment of the containerized application on OKE.
You want to carry out a steady migration to the Oracle Cloud Infrastructure (OCI) platform, making the new microservice functionalities available while maintaining the monolithic application for all the other activities. You also want to integrate the legacy monolithic application with the new microservices to have a single interface with simplified management for auditing and monitoring while meeting operational and compliance requirements.
How can you meet this requirement?
To migrate legacy monolithic applications into cloud-native containerized RESTful microservices on Oracle Cloud Infrastructure (OCI), the most appropriate approach is to utilize serverless technologies and API gateways. Pushing the container image to Oracle Cloud Infrastructure Registry (OCIR) ensures that the containerized application is stored in a central, managed registry. Building a serverless function with OCI Functions using the Bring-Your-Own-Dockerfile (BYOD) feature allows you to deploy the new microservices in a fully serverless environment. Creating an API deployment specification with these serverless functions as the back-end and using an OCI API gateway to provide front-end access ensures you have a single interface for managing and monitoring both the monolithic and microservices components. This approach meets the requirements for ease of integration, simplified management, auditing, and monitoring, while also ensuring compliance.
Oracle Cloud Infrastructure (OCI) Autonomous Transaction Processing - Serverless (ATP-S) deployment is well-suited for scenarios where there is variable and unpredictable workload, need for a managed database service, and cost efficiency. In scenario A, the online auction marketplace experiences unpredictable peaks, which ATP-S can handle dynamically. In scenario D, the developer needs the database only during work hours, allowing costs to be kept low as ATP-S can scale up and down automatically. In scenario E, the startup's uncertain workload can benefit from ATP-S as it provides the flexibility to handle varying loads without a significant upfront investment in database infrastructure.
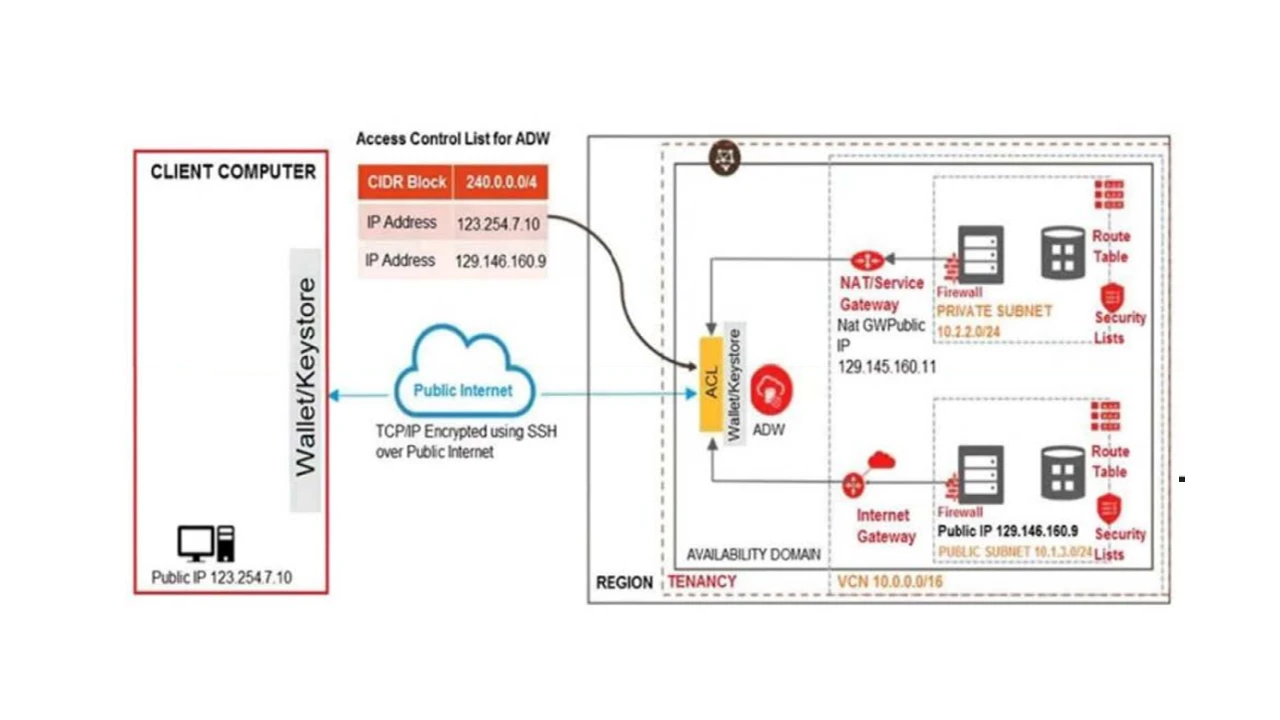
As you are testing the connectivity to your ADW database from the different access paths, you notice that the server running on the private network is unable to connect to ADW.
Which two steps do you need to take to enable connectivity from the server on the private network to ADW? (Choose two.)
To enable connectivity from the private network to the ADW, you need to ensure two things: First, the ADW's security list must allow ingress traffic from the private network's CIDR block (10.2.2.0/24). Second, since the private subnet does not have direct Internet access, you need to route the traffic via a NAT Gateway, adding an entry in the route table associated with the private subnet with a destination of 0.0.0.0/0 and a target type of NAT Gateway. Additionally, a stateful egress rule must be added to the security list associated with the private subnet to allow all IP protocols to the destination 0.0.0.0/0.