You developed an alternative archival solution using Oracle Cloud Infrastructure (OCI) that will save the company a significant amount of money on a yearly basis.
The solution involves storing data in an OCI Object Storage bucket. After reviewing your solution with the customer Global Risk and Compliance (GRC) team, they highlighted four security requirements:
✑ All data less than 1 year old must be accessible within 2 hours
✑ All data must be retained for at least 10 years and be accessible within 48 hours
✑ All data must be encrypted at rest
✑ No data may be transmitted across the public internet
Which two options meet the requirements outlined by the customer GRC team? (Choose two.)
To meet the security requirements, the data must not be transmitted across the public internet and be accessible within specified time limits while ensuring encryption at rest. Option A, provisioning a FastConnect link and configuring a private peering virtual circuit, ensures that data is transmitted securely without using the public internet. Option C involves creating an OCI Object Storage Standard tier bucket with a lifecycle policy to archive objects older than 365 days, fulfilling the requirement to store data for at least 10 years while making it accessible within 48 hours. This combination meets the GRC team's requirements.
The servers are unable to reach the internet. An Internet Gateway has been deployed in the public subnet in the VCN and the appropriate routes are configured in the Route Table associated with the public subnet.
Based on cost considerations, which option will fix this issue? (Choose the best answer)
To allow Oracle Linux servers in a private subnet to access the internet for security patches while minimizing costs, the best solution is to create a NAT gateway in the VCN and configure it as the route target for the private subnet. A NAT gateway allows private subnet instances to access the internet securely and avoids the cost and complexity of managing a NAT instance in the public subnet or using a public load balancer. Additionally, creating another Internet Gateway or using a Public Load Balancer is not appropriate for instances in a private subnet needing outbound internet access and may incur additional costs.
Which three options can you implement together to accomplish this? (Choose three.)
To manage costs and gain insights into department usage of Oracle Cloud Infrastructure (OCI) resources, the following can be implemented: Creating a budget that matches your commitment amount along with an alert at 100% of the forecast provides early warning if spending increases. Setting up different compartments for each department allows for tracking and analyzing costs per department. Using a tag default to automatically apply tags to resources created in a compartment helps in detailed cost analysis by enabling resource tracking through tags.
Which three tasks would enable you to connect to the console connection and begin troubleshooting? (Choose three.)
To connect to the console connection and begin troubleshooting, you should stop the compute instance using the Oracle Cloud Infrastructure (OCI) Command Line Interface (CLI). This allows for changes to take effect. Next, upload an API signing key for console connection authentication to validate your access. Finally, use SSH to connect to the service endpoint of the console connection service, as this is the standard method to establish the connection required for troubleshooting. Editing the Linux boot menu to enable access to the console is unnecessary, rebooting the compute instance does not directly facilitate console access troubleshooting, and providing the console connection OCID as the username is incorrect usage.
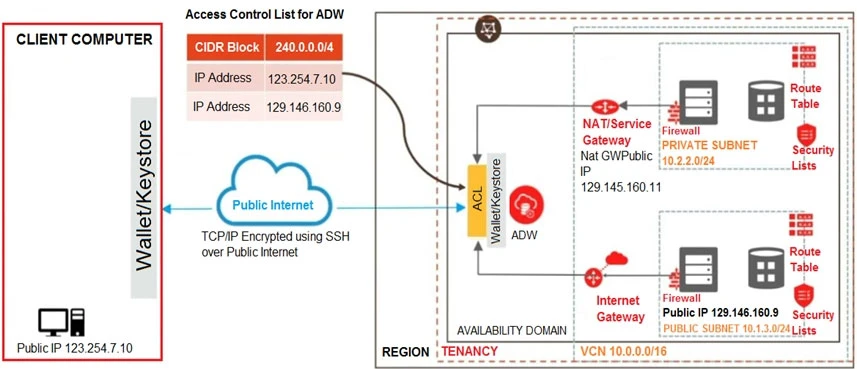
As you are testing the connectivity to your ADW database from the different access paths, you notice that the server running on the private network is unable to connect to ADW.
Which two steps do you need to take to enable connectivity from the server on the private network to ADW? (Choose two.)
To enable connectivity from the server on the private network to the Autonomous Data Warehouse (ADW), you need to add an entry in the route table associated with the private subnet for routing the traffic through the NAT Gateway, and you need to update the access control list (ACL) of ADW to include the IP address of the NAT Gateway. Adding an entry in the route table with a destination of 0.0.0.0/0 and the target type of NAT Gateway allows the private subnet to route traffic to external networks using the NAT Gateway. Including the NAT Gateway's public IP address in the ACL ensures that ADW can accept connections from the private network routed through the NAT Gateway. Option A, which suggests modifying the security list of ADW, is not correct because ADW does not have security lists; it uses ACLs to control access.