How can an alert be set up that is guaranteed to trigger AS SOON AS that API implementation stops responding to API invocations?
What is a valid approach that minimizes the impact of this change on API clients?
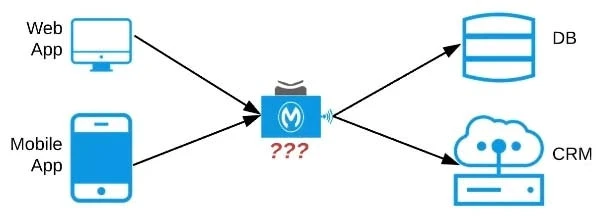
An organization needs to enable access to their customer data from both a mobile app and a web application, which each need access to common fields as well as certain unique fields.
The data is available partially in a database and partially in a 3rd-party CRM system.
What APIs should be created to best fit these design requirements?

A developer is building a client application to invoke an API deployed to the STAGING environment that is governed by a client ID enforcement policy.
What is required to successfully invoke the API?