You are informed about incidents that relate to compromised identities.
You need to recommend a solution to expose several accounts for attackers to exploit. When the attackers attempt to exploit the accounts, an alert must be triggered.
Which Defender for Identity feature should you include in the recommendation?
To expose several accounts for attackers to exploit and trigger an alert upon exploitation, the recommended feature is honeytoken entity tags. Honeytoken entities act as traps for malicious actors; any authentication attempt associated with these honeytoken entities triggers an alert, making them the ideal solution for this scenario.
You need to design a security orchestration, automation, and response (SOAR) strategy in Microsoft Sentinel that meets the following requirements:
✑ Minimizes manual intervention by security operation analysts
✑ Supports triaging alerts within Microsoft Teams channels
What should you include in the strategy?
Playbooks in Microsoft Sentinel are designed to automate and orchestrate threat response actions, which helps minimize the need for manual intervention by security operation analysts. They are essentially workflows that can be built using Azure Logic Apps, allowing you to define a series of automated steps to take when specific alerts or incidents are triggered. Furthermore, Playbooks can be integrated with Microsoft Teams, facilitating the triaging of alerts within Teams channels. This makes Playbooks the best fit for a Security Orchestration, Automation, and Response (SOAR) strategy that aims to minimize manual efforts and support alerts management within Microsoft Teams.
All resources are backed up multiple times a day by using Azure Backup.
You are developing a strategy to protect against ransomware attacks.
You need to recommend which controls must be enabled to ensure that Azure Backup can be used to restore the resources in the event of a successful ransomware attack.
Which two controls should you include in the recommendation? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
To protect against ransomware attacks and ensure that Azure Backup can be used to restore resources, two important controls should be enabled. First, enabling soft delete for backups ensures that deleted backup data is retained for a certain period (14 days by default for Azure VMs), which allows recovery even if backups are deleted maliciously. Second, requiring PINs for critical operations adds an extra layer of security by ensuring that only authorized users can perform sensitive actions like deleting backup data or changing backup configurations. This helps prevent unauthorized access and protects data integrity.
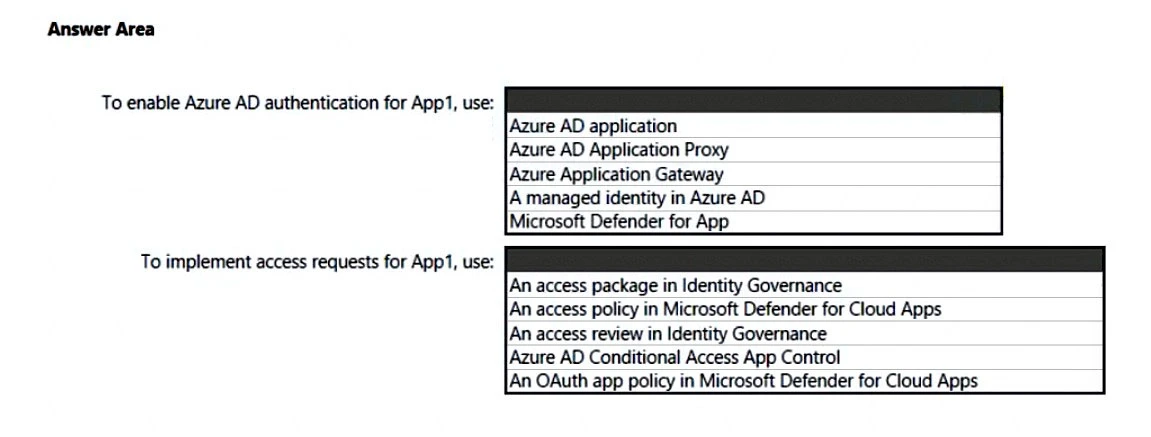
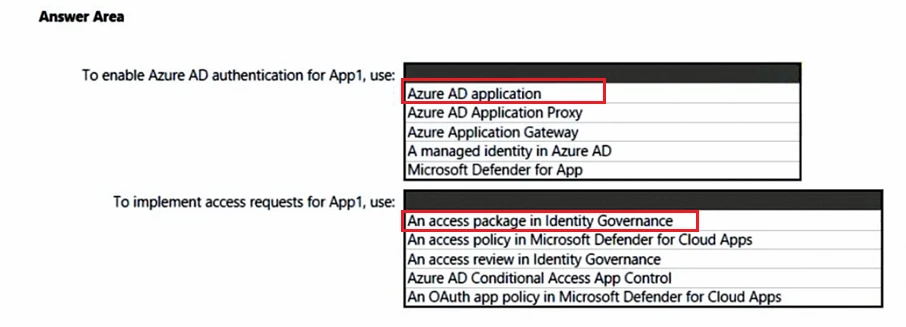
You are creating the security recommendations for an Azure App Service web app named App1. App1 has the following specifications:
✑ Users will request access to App1 through the My Apps portal. A human resources manager will approve the requests.
✑ Users will authenticate by using Azure Active Directory (Azure AD) user accounts.
You need to recommend an access security architecture for App1.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Your company uses Microsoft Defender for Cloud and Microsoft Sentinel.
The company is designing an application that will have the architecture shown in the following exhibit.
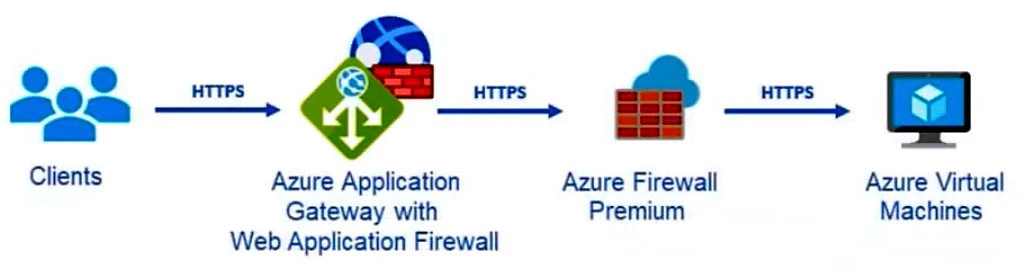
You are designing a logging and auditing solution for the proposed architecture. The solution must meet the following requirements:
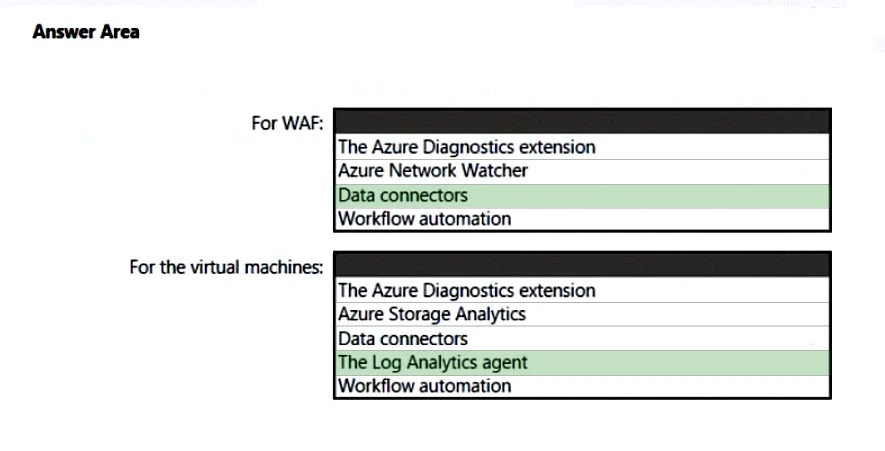
✑ Integrate Azure Web Application Firewall (WAF) logs with Microsoft Sentinel.
✑ Use Defender for Cloud to review alerts from the virtual machines.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
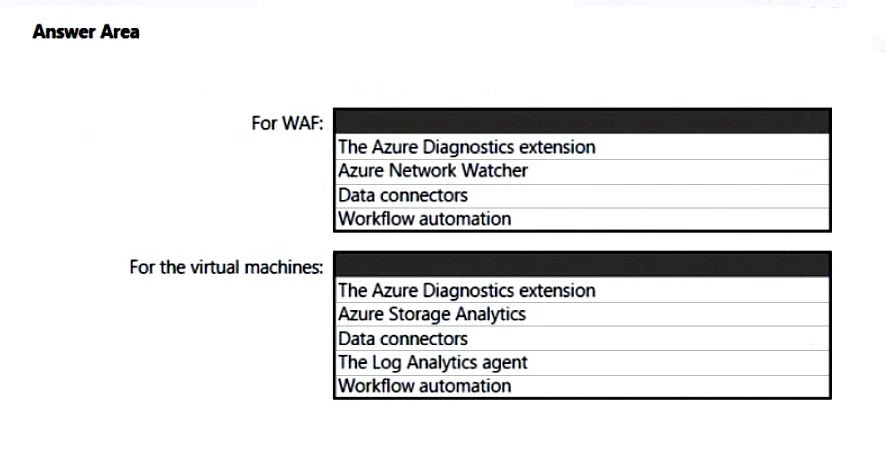
Microsoft Sentinel connector streams security alerts from Microsoft Defender for Cloud into Microsoft Sentinel.
Launch a WAF workbook (see step 7 below)
The WAF workbook works for all Azure Front Door, Application Gateway, and CDN WAFs. Before connecting the data from these resources, log analytics must be enabled on your resource.
To enable log analytics for each resource, go to your individual Azure Front Door, Application Gateway, or CDN resource:
1. Select Diagnostic settings.
2. Select + Add diagnostic setting.
3. In the Diagnostic setting page (details skipped)
4. On the Azure home page, type Microsoft Sentinel in the search bar and select the Microsoft Sentinel resource.
5. Select an already active workspace or create a new workspace.
6. On the left side panel under Configuration select Data Connectors.
7. Search for Azure web application firewall and select Azure web application firewall (WAF). Select Open connector page on the bottom right.
8. Follow the instructions under Configuration for each WAF resource that you want to have log analytic data for if you haven't done so previously.
9. Once finished configuring individual WAF resources, select the Next steps tab. Select one of the recommended workbooks. This workbook will use all log analytic data that was enabled previously. A working WAF workbook should now exist for your WAF resources.
Box 2: The Log Analytics agent -
Use the Log Analytics agent to integrate with Microsoft Defender for cloud.
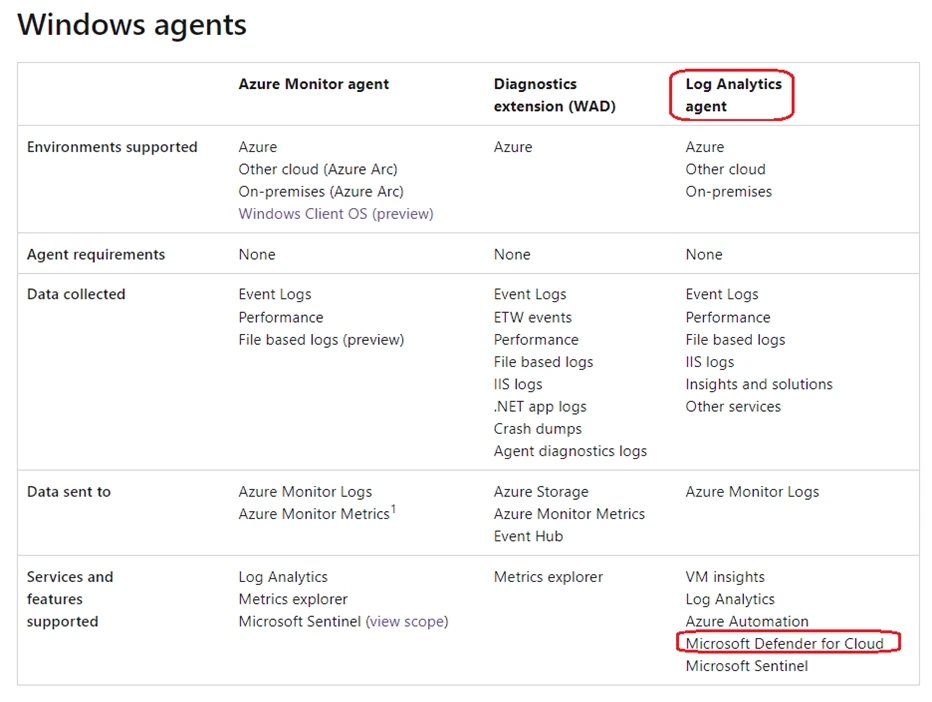
The Log Analytics agent is required for solutions, VM insights, and other services such as Microsoft Defender for Cloud.
Note: The Log Analytics agent in Azure Monitor can also be used to collect monitoring data from the guest operating system of virtual machines. You may choose to use either or both depending on your requirements.
Azure Log Analytics agent -
Use Defender for Cloud to review alerts from the virtual machines.
The Azure Log Analytics agent collects telemetry from Windows and Linux virtual machines in any cloud, on-premises machines, and those monitored by System
Center Operations Manager and sends collected data to your Log Analytics workspace in Azure Monitor.
Incorrect:
The Azure Diagnostics extension does not integrate with Microsoft Defender for Cloud.
Reference:
https://docs.microsoft.com/en-us/azure/web-application-firewall/waf-sentinel https://docs.microsoft.com/en-us/azure/defender-for-cloud/enable-data-collection https://docs.microsoft.com/en-us/azure/azure-monitor/agents/agents-overview