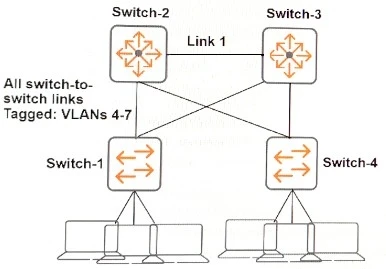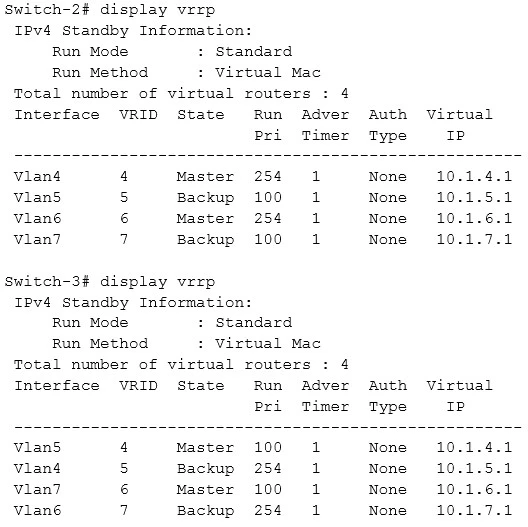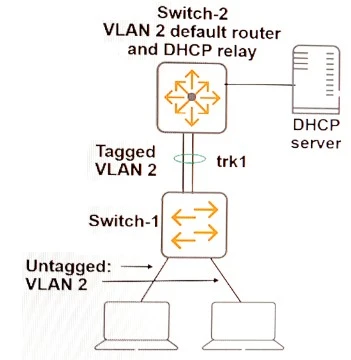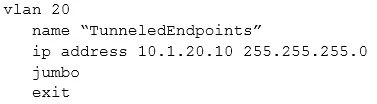
A network administrator needs to deploy AOS-Switches that implement port-based tunneled node. Their Aruba controller has IP address 10.1.10.5/24. The architect has assigned tunneled-node endpoints to VLAN 20.
What is one issue with the current configuration planned for VLAN 20 on the switch?