What section of the penetration test or ethical hacking engagement final report is used to detail and prioritize the results of your testing?
The section of a penetration test or ethical hacking engagement final report used to detail and prioritize the results of your testing is the 'Findings' section. This part of the report summarizes the discovered vulnerabilities, their impact, and prioritizes them based on their severity, helping stakeholders understand the critical areas that need immediate attention.
You are pen testing a Windows system remotely via a raw netcat shell. You want to quickly change directories to where the Windows operating system resides, what command could you use?
To change directories to where the Windows operating system resides, you would use the command 'cd %systemroot%'. The '%systemroot%' environment variable in Windows points to the root directory of the Windows operating system, typically 'C:\Windows'. None of the other options correctly utilize this environment variable.
A client with 7200 employees in 14 cities (all connected via high speed WAN connections) has suffered a major external security breach via a desktop which cost them more than SI 72.000 and the loss of a high profile client. They ask you to perform a desktop vulnerability assessment to identify everything that needs to be patched. Using Nessus you find tens of thousands of vulnerabilities that need to be patched. In the report you find workstations running several Windows OS versions and service pack levels, anti-virus software from multiple vendors several major browser versions and different versions of Acrobat Reader. Which of the following recommendations should you provide with the report?
The client should standardize their desktop software. By standardizing, the organization can significantly reduce the complexity and variety of software that needs to be managed and patched. This approach leads to more efficient and consistent patch management processes, reducing vulnerabilities and potential points of entry for security breaches. It helps in creating a uniform security policy and makes vulnerability assessments and management easier and more effective in the long run.
Which Metasploit payload includes simple upload and download functionality for moving files to and from compromised systems?
Meterpreter is a powerful and extensible payload that provides complex and useful functionality, including the ability to upload and download files to and from a compromised system.
A junior penetration tester at your firm is using a non-transparent proxy for the first time to test a web server. He sees the web site In his browser but nothing shows up In the proxy. He tells you that he just installed the non-transparent proxy on his computer and didn't change any defaults. After verifying the proxy is running, you ask him to open up his browser configuration, as shown in the figure, which of the following recommendations will correctly allow him to use the transparent proxy with his browser?
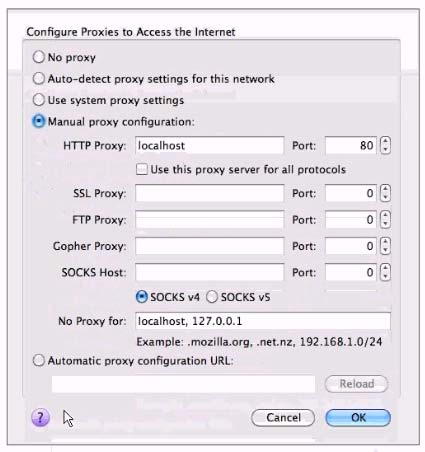
The junior penetration tester can see the website in his browser but nothing shows up in the proxy because the port might not be correctly configured. The non-transparent proxy, also known as an explicit proxy, requires the browser to be configured to send traffic to the proxy's port. The default value shown in the HTTP proxy port field is 80, which is typically reserved for HTTP traffic and may not be the port the non-transparent proxy is listening on. To correctly use the non-transparent proxy with his browser, he should change the port value to match the port used by the non-transparent proxy.