Is the following code vulnerable to SQL Injection where ($mysqli is an instance of the MySQLi class)?
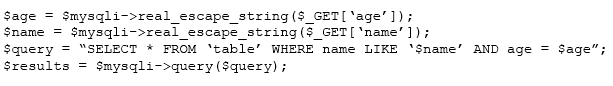
Is the following code vulnerable to SQL Injection where ($mysqli is an instance of the MySQLi class)?

The provided code is vulnerable to SQL Injection because while `real_escape_string` helps mitigate the risk of injection by escaping special characters, it doesn't provide full protection. Specifically, although `$name` is escaped and enclosed in single quotes, making this portion relatively safe, `$age` is not enclosed in quotes in the SQL query. This means that an attacker could potentially inject SQL logic through the `$age` parameter. To fully prevent SQL Injection, parameterized queries should be used. Both `$name` and `$age` are at risk as escaping alone does not guarantee security if the values are not handled correctly. Thus, the correct answer is that both `$name` and `$age` are improperly escaped.
The answer is really D. Because $age can be: $age = "1 or admon = 1" and this is kind of sql injection that is not prevented. $name is single quoted inside sql query, so it prevents this sql injection.