Refer to the exhibit.
What is required to fix the PSOD?
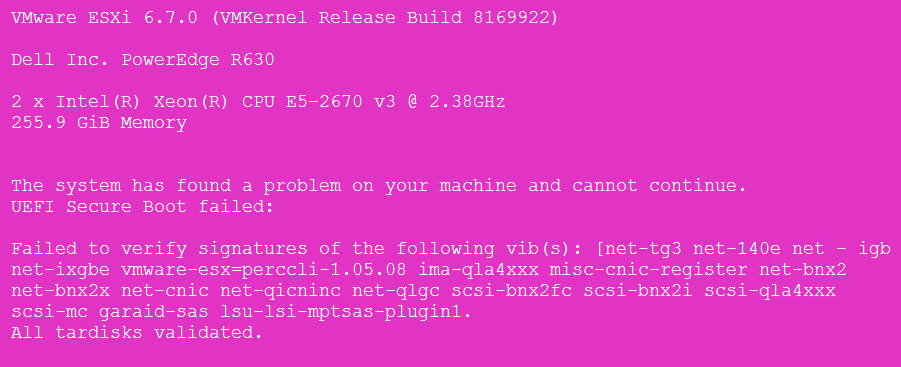
Refer to the exhibit.
What is required to fix the PSOD?

The issue described in the PSOD (Purple Screen of Death) is related to the failure of UEFI Secure Boot due to the presence of unsigned VIBs (vSphere Installation Bundles). To resolve this, the offending unsigned VIBs need to be removed from the system. Once these unsigned VIBs are removed, the secure boot can function correctly, and the system can boot normally. Rebooting the host or enabling secure boot from the UEFI firmware interface without removing the unsigned VIBs will not resolve the issue, as the secure boot process will continue to fail due to the verification of these VIBs.
The unsigned VIBs need to be removed. Secure Boot is already enabled and is failing. https://blogs.vmware.com/vsphere/2018/06/prepping-an-esxi-6-7-host-for-secure-boot.html
Correct answer C. Checked in exam.
In the KB below, they simply remove the offending VIBs and then trying to perform secure boot again. So I guess the answer would be "C" https://kb.vmware.com/s/article/54481
I believe the answers is "C"
Correct answer C. Checked in egzam.
Correct answer is C https://kb.vmware.com/s/article/54481
I would go for C. D is very wrong, because it is secure boot is already enabled, hence the PSOD.
C is the right answer. You need to remove the unsigned vibs, then you may enable secure boot. The provided link still valid.. Just read it to confirm what I said
Correct Answer is C. Here is the reference, https://blogs.vmware.com/vsphere/2018/06/prepping-an-esxi-6-7-host-for-secure-boot.html
If a package (VIB or driver) has been tampered with, a purple screen with the following message appears. UEFI Secure Boot failed: Failed to verify signatures of the following vibs (XX) To resolve issues with secure boot, follow these steps. 1 Reboot the host with secure boot disabled. 2 Run the secure boot verification script (see Run the Secure Boot Validation Script on an Upgraded ESXi Host). 3 Examine the information in the /var/log/esxupdate.log file. n If old VIBs remain on the system, the signatures of those VIBs are not available and secure boot is not possible. n If the system uses a third-party driver, and the VMware upgrade does not include a new version of the driver VIB, then the old VIB remains on the system after upgrade. vSphere Security VMware, the answers is "C"
Remove VIBs first, then lastly reboot and enable secure boot from the UEFI firmware interface. Answer=C
A != not such option B != restarting host will bring same result C != you need to log in to esx to remove offending vibs (and its failing to boot). If you boot esx from different source it will load vibs from that source (not one you are troubleshoot). D = the only option that will allow you to load esx and run esxcli software vib remove -n offending_name plugin == remove offending vibs (option C). D
UEFI Secure Boot is already enabled. So enable secure boot is not an option.
Answer is C, found in PSOD’s, unsigned VIBs and File Integrity Monitoring (FIM) of link : -Restart and turn off Secure Boot in the UEFI firmware and boot the host with Secure Boot turned off. -When booted, log into the host and remove the offending VIB and shutdown. -Re-enable Secure Boot and restart the host and the system should boot normally. https://blogs.vmware.com/vsphere/2017/05/secure-boot-esxi-6-5-hypervisor-assurance.html
Correct answer is C 1- Remove the lsu-lsi-mptsas-plugin VIB 2- Reboot and enable secure boot from the UEFI firmware interface. Ref: https://kb.vmware.com/s/article/2147606
The question is "How do you resolve the PSOD". Is does not ask about how to resolve the issue highlighted by the PSOD only how to resolve the PSOD itself. Therefore you woul dneed to "Reboot the host". Of course the other "correct" answers are achievable but only after you have rebooted the host.
If you only reboot the host, you get PSOD again
D is correct https://kb.vmware.com/s/article/2147606