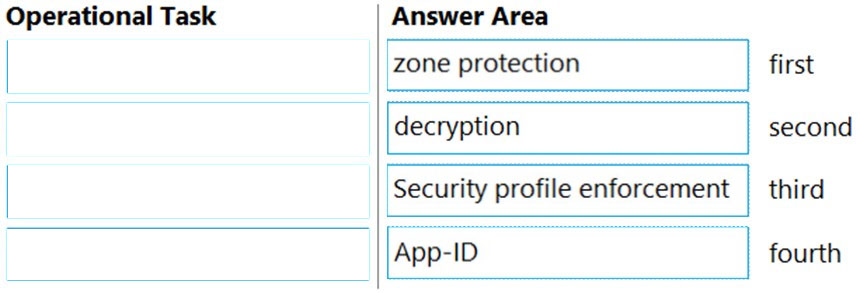
DRAG DROP -
Place the steps in the correct packet-processing order of operations.
Select and Place:

DRAG DROP -
Place the steps in the correct packet-processing order of operations.
Select and Place:

Reference:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClVHCA0
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClVHCA0 1. Zone protection 2. Decryption 3. App-ID 4. Security profile enforcement
I gree. Best explanation: https://networkinterview.com/packet-flow-in-palo-alto-detailed-explanation/
@blackisok Based on the link you provided this is incorrect. Decryption should be first as it is done in the Tunnel decapsulation of the the Ingress Stage. Zone Protection checks is done in the next Firewall Session Lookup Stage. Then Security Policy, then App-ID. So based on your link it should be 1. Decryption 2. Zone Protection 3. Security Profile 4. App-ID
i think this is it too. Security profile should come first before App-ID. If not what App-ID does it know to check if it does not see the profile first.
I believe that it goes in this order 1.Decryption 2.Zone protection 3.Security profile enforcement 4.App-ID
This seems right to me. Not sure why people are saying Zone protection comes first. The Palo Alto doc says that it's 3.1 - after decryption.
1. Zone protection 2. Decryption 3. App id 4. Security profile enforcement
This is correct
Zone Protection Checks TCP State Check Forwarding (based on interface type) NAT Policy Lookup (only L3 & Virt wire) DoS Protection Policy Lookup Security Policy Lookup Session Allocation Firewall Session Fast Path (if packet from existing session) Security Processing Captive Portal Application Identification Content Inspection Forwarding/Egress (includes QoS)
Where would you say that decryption process is taking place?
I would say it would have to be taking place first or else the contents of the packet wouldnt be able to be read to determine the remaining Zone/Security/App info.
https://networkinterview.com/packet-flow-in-palo-alto-detailed-explanation/
The packet processing order in Palo Alto Networks firewalls typically follows these steps: Packet Ingress: Zone Protection: This is where the firewall evaluates if the packet complies with the security policies defined for the source and destination zones. Decryption: If the traffic is encrypted, the firewall decrypts the packet to inspect the decrypted content. Decryption is often performed using SSL decryption policies. App-ID (Application Identification): The firewall identifies the application associated with the traffic. This is a crucial step in allowing or blocking traffic based on the specific applications being used. Security Profile Enforcement: After the application is identified, security profiles (such as antivirus, anti-spyware, and vulnerability protection) are applied to the traffic to detect and prevent threats.
This question is confusing as f*ck. It all depends on wether decryption is based on ssl proxy or VPN traffic And wether a session already exists or not. So if this would be adressing a NEW session of SSL Proxy traffic, the order should be 1. Zone protection 2. Decryption 3. App-ID 4. Security profile enforcement
Decryption Zone protection App-ID Security profile enforcement
I think it should be Decryption, Zone Protection, App-ID then Security Profile enforcement. See link below. https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClVHCA0
1. Zone protection 2. Security profile enforcement 3. Decryption 4. App id