In the image, what caused the commit warning?
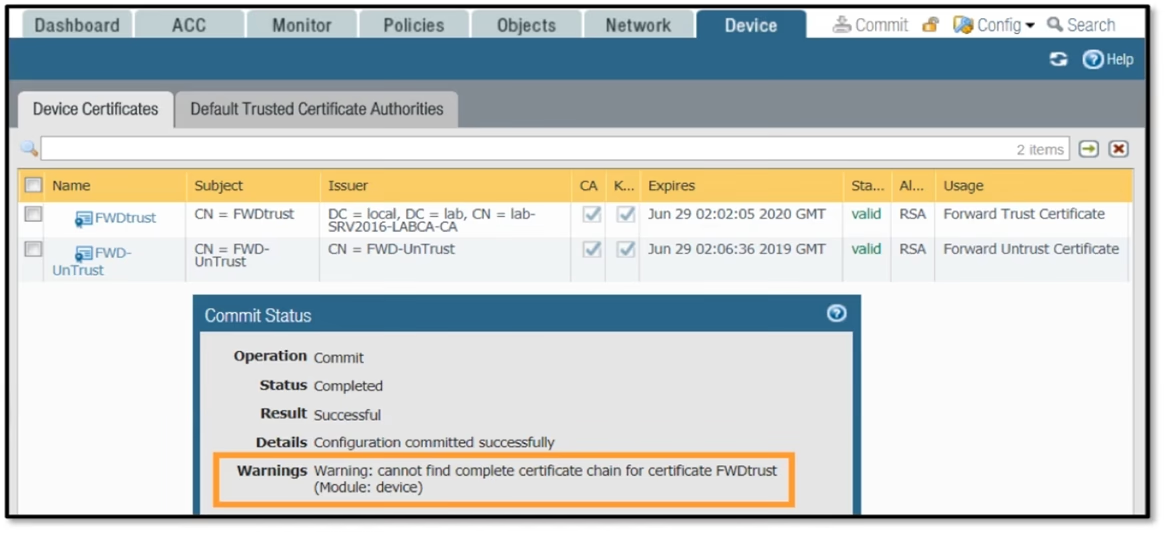
In the image, what caused the commit warning?

The warning message 'cannot find complete certificate chain for certificate FWDtrust' suggests that the firewall is unable to establish a complete chain of trust for the FWDtrust certificate. This usually happens when the firewall does not have the necessary CA (Certificate Authority) certificates to verify the FWDtrust certificate. In this case, the FWDtrust certificate is likely signed by an intermediate CA certificate, which in turn must be signed by a root CA certificate. Therefore, the CA certificate that signed the FWDtrust certificate has not been imported into the firewall, causing the inability to complete the certificate chain.
Option A. The FWDtrust is a CA certificate type capable of signing other certificates. That means either it's a Root Certificate or Intermediate certificate. If it was a Root Certificate, then you wouldn't get that warning. That means the certificate is an intermediate and you need to import its Root Certificate.
correct, in addition, the CA for FWDtrust is some LAB CA, says it under issuer, so definitely not root
The answer is D. When importing a CA certificate, the full certificate chain must be present in the certificate information for proper identification/verification. A can't be true because the certificate in question is imported is a CA cert. B can't be true because the certificate in question is imported as a trusted root CA. C can't be true because SSL Forward proxy can be set up using self-signed certs. https://docs.paloaltonetworks.com/pan-os/10-0/pan-os-admin/decryption/configure-ssl-forward-proxy.html
correct!
Agreed
Agreed
The certificate in the screenshot is a CA, because it has to be a CA for forward trust. The issue is that FWDTrust's (Which is CN = "Lab-SRV2016...") does not have its CA imported. If it were the CA of its chain, the subject would match the issuer.
A. Tested in lab.
A - Tested in lab
A is inacurate, no need to be a Trust root CA
I think answer is A : is not self-signed-certificate -> so other certificate signed this certificate, if that is not imported there is no chain of trust
A: https://docs.paloaltonetworks.com/pan-os/10-0/pan-os-admin/decryption/troubleshoot-and-monitor-decryption/decryption-logs/repair-incomplete-certificate-chains.html
A. because FWDtrust has a chain but it's not present in the firewall.
Hi Team to add It is A as other users have done I tested this as well. If you're using an External/Internal PK, you need to ensure to import the Root CA, in which once you create, generate your CSR, and reimport the Trust cert into the Firewall. The Turst cert should fall into the COC. If this was a self-signed cert (as I have also labbed) you can simple have that on the FW without a COC.
D. The problem, as it says itself, is that it does not have a complete chain of trust. The solution would be to add in any intermediate CAs that the NGFW doesn't have as root CAs to restore the chain, but the problem is the chain.
D is ambiguous. D is saying that there is no certificate chain for that cert, but there is because the issuer for the FWDTrust is not the same CN as the subject of FWDTrust
D is the answer. It is a simple warning that states that there is no chain
D here aslo, FWDtrust cert has been imported but the firewall could not verify it and asks for the Cert Chain (import either Root or Intermediate that validates FWDtrust)
D is the answer because the image show us the CA and Key checkboxes, telling us that is a self signed Root CA without a certificate, in other words without a chain and according to warning show in screen.
If you look at the subject, you will see that there's another certificate which signs the FWDtrust. In fact, it is not a self signed certificate because of that statement, so D is ambigous compared to A, because the FWDtrust does has a certificate chain, just that it's not -imported- into the fw.
I think it should be B,
The answer is A. The issuer of the cert was not imported in the firewall and the firewall could not build a chain because of it.
A. because FWDtrust has a chain but it's not present in the firewall.
Option A.
I think the correct answer is B.
I think the correct answer is B.
Under issuer, it tells us which root CA signed the FWDTrust certificate. Correct answer is A. FWDTrust needs to be a CA (intermediate in this case) in order for it to be able to sign the server certs so that clients accessing an external server or website can tell if the firewall trusts those server certs or not.
Subject CN and issuer CN are different, therefore this certificate is signed by someone else and need to be present in order to complete the chain
Look at Usage Tab, we are missing Root CA, First cert is used as Forward Trust and 2nd one is used for Forward untrust
Answer A is correct: It is only best practice, not mandatory, to import the full certificate chain for a forward trust certificate, and hence only a warning, not a commit failure. Answer D is incorrect: The certifictae DOES have an issuer - see the "Issuer" field.
Both A and D are correct if there are no intermediate CAs between FWDTrust and Root CA. However if there is one or more Intermediate CA-s between them then only D is correct.