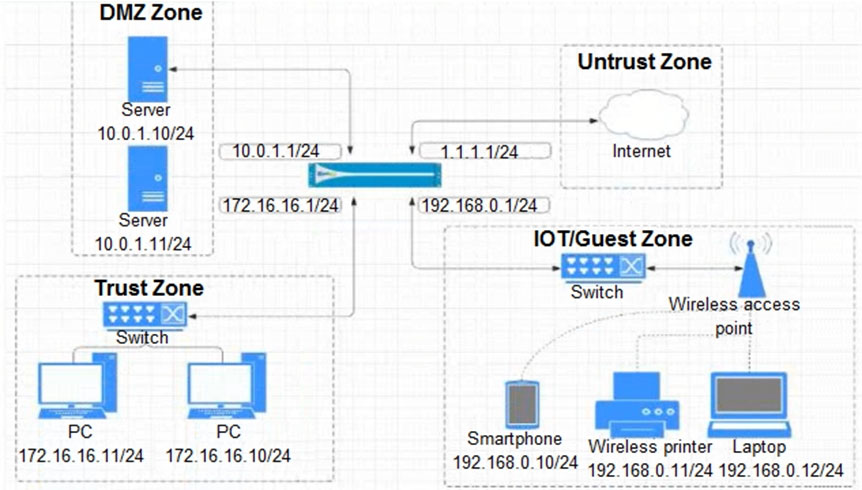
Given the network diagram, traffic should be permitted for both Trusted and Guest users to access general Internet and DMZ servers using SSH, web-browsing and SSL applications.
Which policy achieves the desired results?
A.
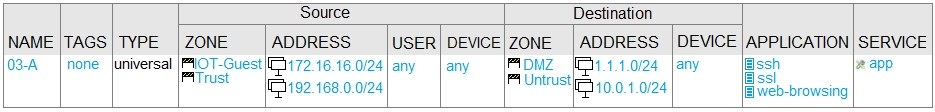
B.
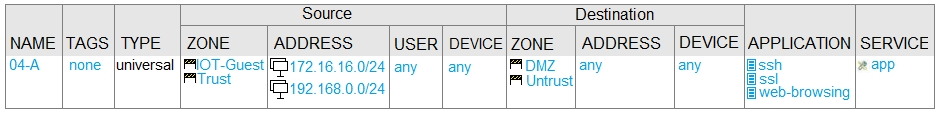
C.
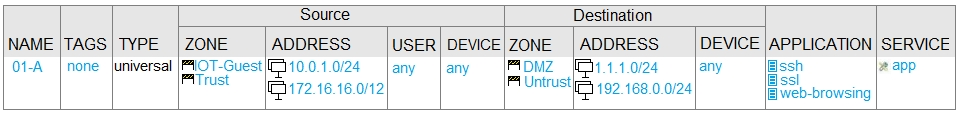
D.
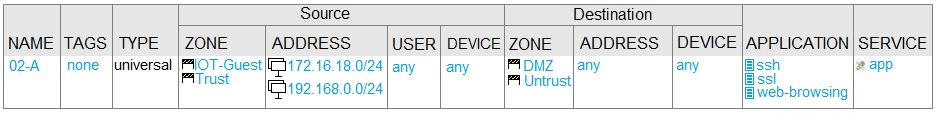

Given the network diagram, traffic should be permitted for both Trusted and Guest users to access general Internet and DMZ servers using SSH, web-browsing and SSL applications.
Which policy achieves the desired results?
A.

B.

C.

D.

The correct policy to achieve the desired results is policy B. This policy allows traffic from both the Trusted and IOT/Guest zones to access the DMZ and Untrust zones using SSH, SSL, and web-browsing applications. The source addresses include both 172.16.16.0/24 and 192.168.0.0/24 networks, which correspond to the Trusted and IOT/Guest zones respectively. The destination zones and addresses include both the DMZ zone (10.0.1.0/24) and the Untrust zone (1.1.1.0/24), allowing access to both the internet and the DMZ servers. This policy ensures that all required traffic is permitted as specified in the question.
B. Because A restricts internet to just the nexthop network
B is correct
Shouldn't it be A ?
My bad, B is correct. Because A is too restrictive on internet
i think so A.Because both ip address is colect.
Answer is B
Not A - cause it only allowed the access to 1.1.1.* network.