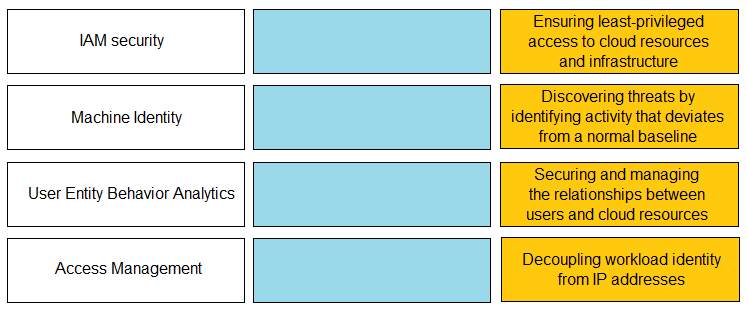
DRAG DROP -
Match the Identity and Access Management (IAM) security control with the appropriate definition.
Select and Place:
DRAG DROP -
Match the Identity and Access Management (IAM) security control with the appropriate definition.
Select and Place:

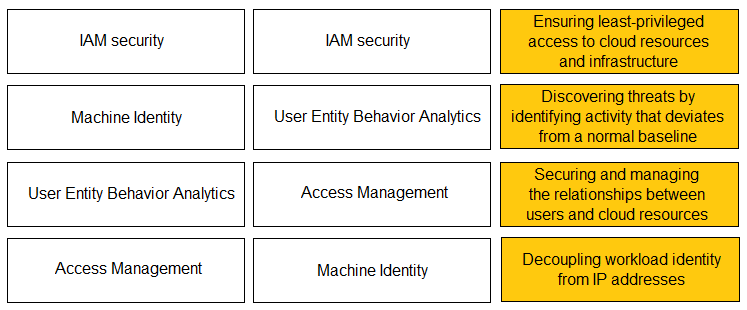
Flip Access managment & IAM Key capabilities include: ● Identity and Access Management (IAM) security: Secure and manage the relationships between users and cloud resources. Enforce governance policies to ensure that users and resources behave only as intended and do not introduce risk to the environment. ● Access management: Ensure least-privileged access to cloud resources and infrastructure, and decouple user permissions from workload permissions. ● Machine identity: Decouple workload identity from IP addresses. Leverage tags and metadata to assign a logical identity to applications and workloads, and then use it to enforce ID-based micro-segmentation and security policies that adapt to your dynamic environments. ● UEBA: Continuously analyze the behavior of users and resources in your cloud to detect and prevent anomalous behavior, such as an admin logging in from an unknown location or a container accessing a file it should not be able to access.
Correct. Found on Page 149 of the study guide.