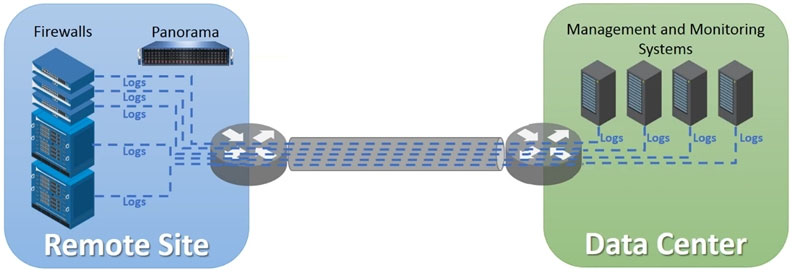
Correct Answer: AIn the given scenario, the network team has reported excessive traffic on the corporate WAN due to the logs being sent from several remote firewalls to multiple monitoring and security management platforms. The best solution to reduce WAN traffic, while still supporting all existing platforms, is to centralize the log forwarding process. By forwarding logs from firewalls only to Panorama and then having Panorama forward logs to the other external services, you can significantly reduce the number of log streams traversing the WAN. This centralized approach minimizes the bandwidth consumption on the WAN link, as Panorama acts as an intermediate log aggregator and distributor. Additionally, it simplifies the log collection and forwarding architecture, leading to more efficient network resource usage and potentially improved overall system performance.