With the default TCP and UDP settings on the firewall, what will be the identified application in the following session?
With the default TCP and UDP settings on the firewall, what will be the identified application in the following session?

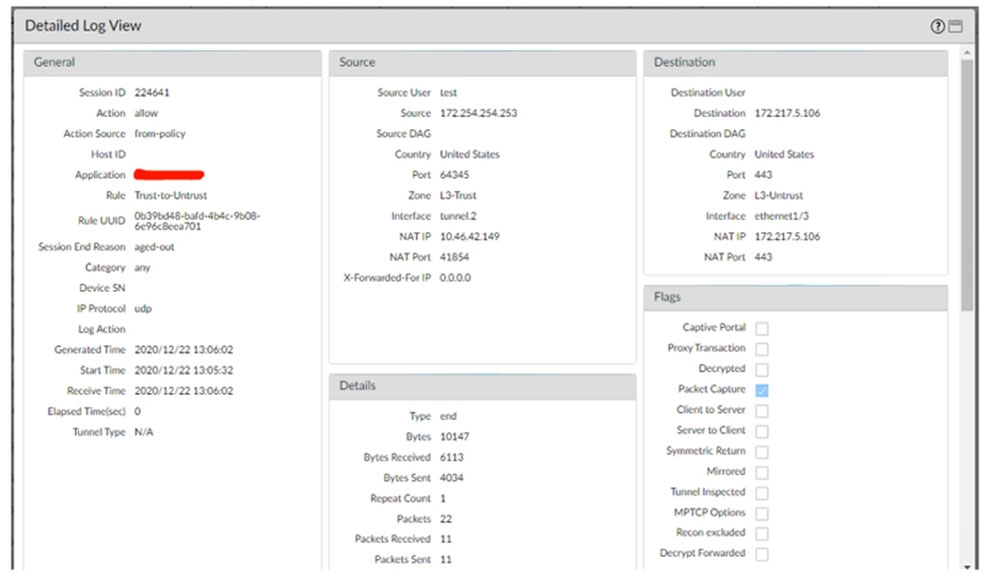
The identified application in this session will be unknown-udp. Since the IP protocol being used here is UDP and the session has been aged-out without a specified application, the firewall defaults to labeling such traffic as unknown-udp. The 'incomplete' application is used only for TCP connections when the TCP three-way handshake is not completed and there is insufficient data to identify the application.
A would be the correct answer here. It is a UDP connection on port 443. This would trigger unknown-udp. Incomplete is used in TCP connections only. https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClibCAC
Not C for sure, base on the red cross line, the answer should be shorter than "Trust-to-Untrust".
Unknown UDP
if is not detected application UDP connection only have two possibilities, not-applicable and unknown-udp or unknown-p2p. The correct answer is A
Unknown UDP
I agree, A is correct.
not-applicable for any deny action. incomplete is for tcp connection with open but not complete 3 way HS, or not enough data to identify the tcp application.(incomplete is used only for tcp connection) now both unknown-udp and insufficint-data are used for udp. againe the question and/or answer are poorly writen. My answer would be both A and C. NOT: A
A seems to be correct. For UDP, the firewall only requires the first packet to identify the app, since its a udp connection on port 443, I would go with unknown-udp
for udp the aplication type can only be unknown-udp or not-aplicable. insuficient-data or incomplete is for TCP. then unknown-udp if the traffic is allowed and not-aplicable if the traffic is not allowed (dicarded). So A should be the correct one.
For it can be both A and C. 11 packets is right in the middle ot 7 to 14 packets rule to detect the app. Stupid question.
A is the correct answer because the protocol being used is udp.
1.https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Clc6CAC-----2.https://live.paloaltonetworks.com/t5/blogs/discussion-of-the-week-application-incomplete/ba-p/286965------<aged-out>
https://live.paloaltonetworks.com/t5/general-topics/application-insufficient-data/td-p/43385
C for sure