HOTSPOT -
Your network contains an on-premises Active Directory domain named adatum.com that syncs to Azure Active Directory (Azure AD).
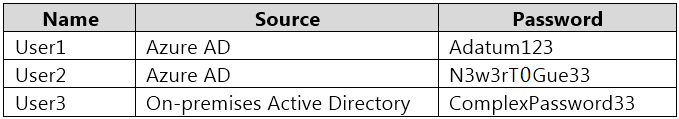
The Azure AD tenant contains the users shown in the following table.
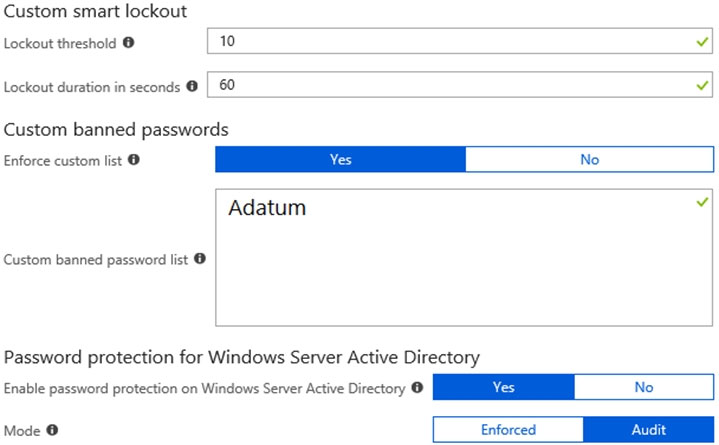
You configure the Authentication methods `" Password Protection settings for adatum.com as shown in the following exhibit.
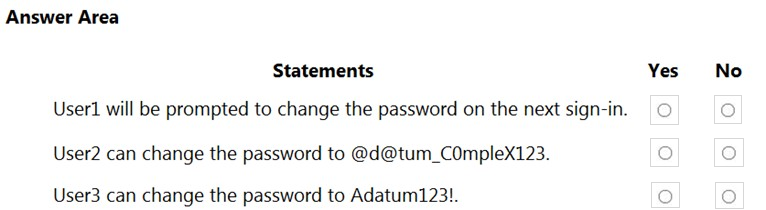
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: