HOTSPOT -
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.

You create and enforce an Azure AD Identity Protection sign-in risk policy that has the following settings:
✑ Assignments: Include Group1, exclude Group2
✑ Conditions: Sign-in risk level: Medium and above
✑ Access: Allow access, Require multi-factor authentication
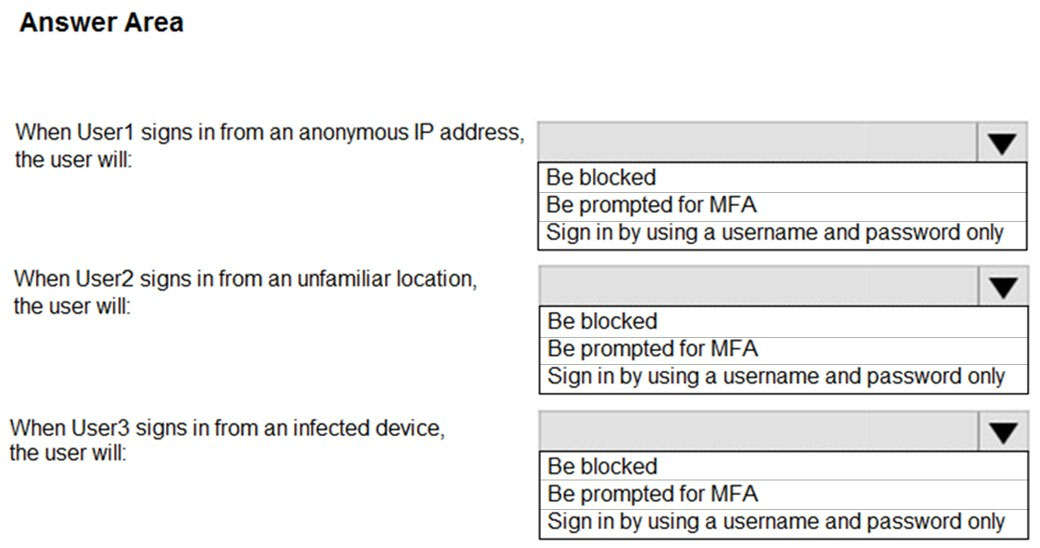
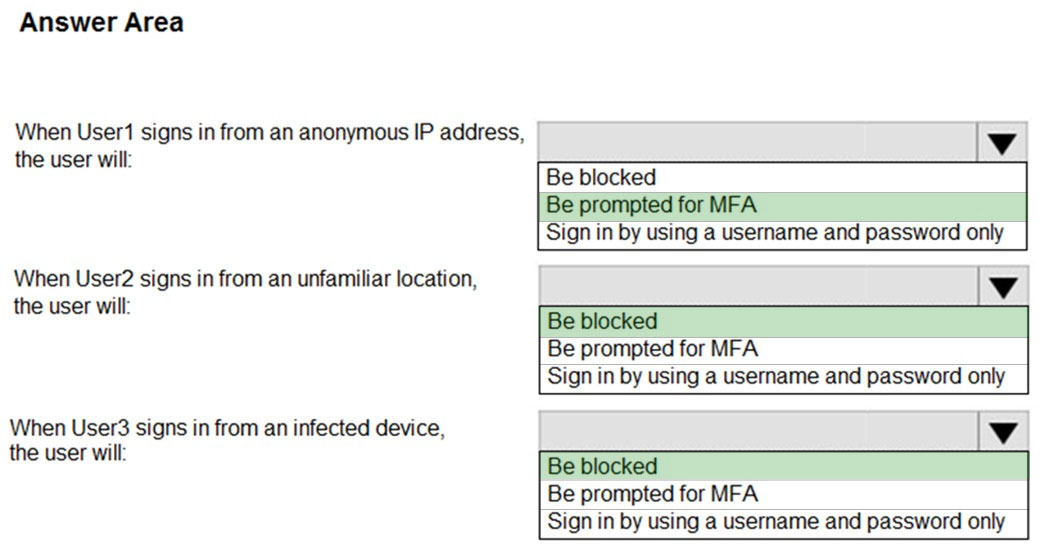
You need to identify what occurs when the users sign in to Azure AD.
What should you identify for each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: