HOTSPOT -
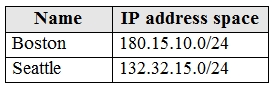
You work at a company named Contoso, Ltd. that has the offices shown in the following table.
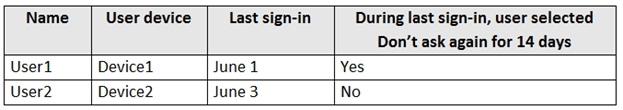
Contoso has an Azure Active Directory (Azure AD) tenant named contoso.com. All contoso.com users have Azure Multi-Factor Authentication (MFA) enabled. The tenant contains the users shown in the following table.
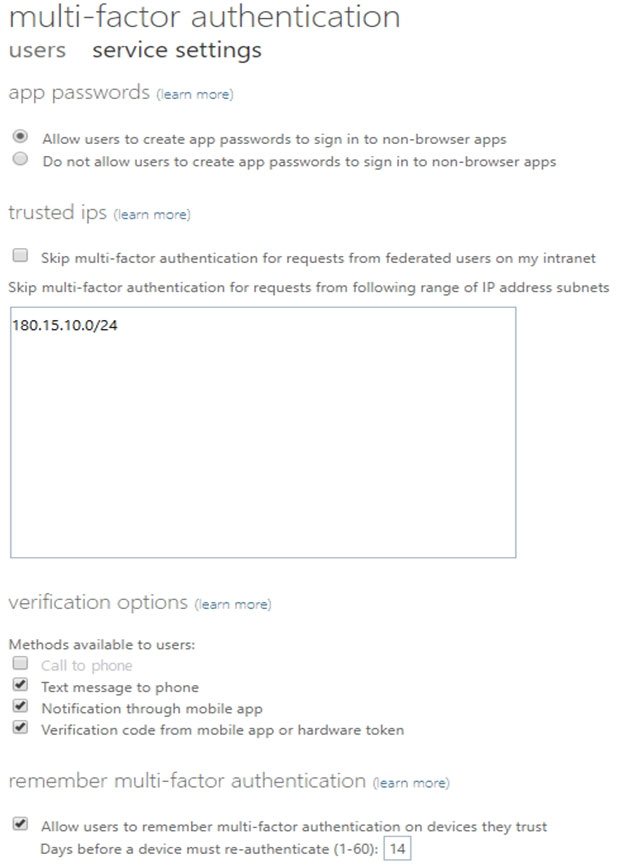
The multi-factor authentication settings for contoso.com are configured as shown in the following exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

