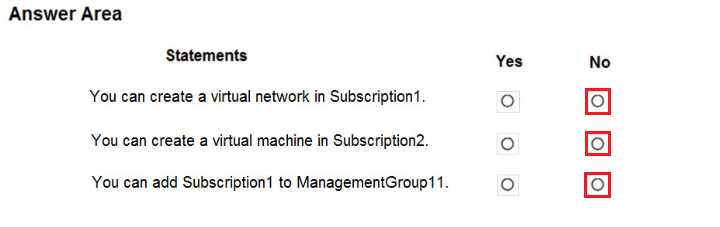
HOTSPOT -
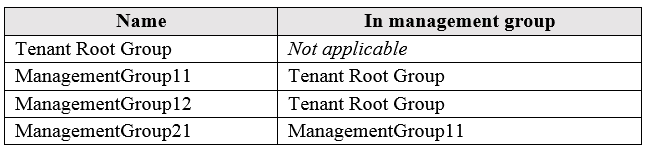
You have the Azure management groups shown in the following table:
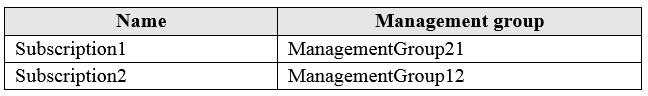
You add Azure subscriptions to the management groups as shown in the following table:
You create the Azure policies shown in the following table:
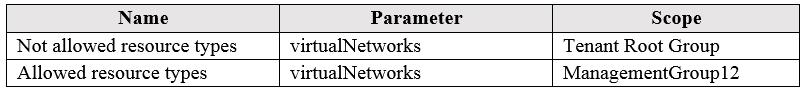
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: