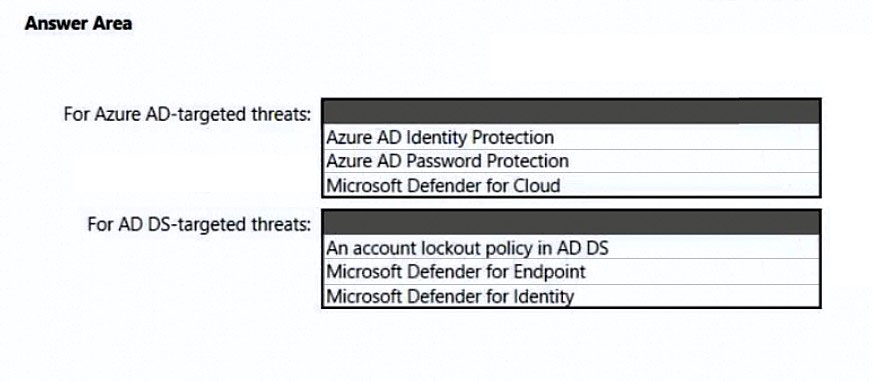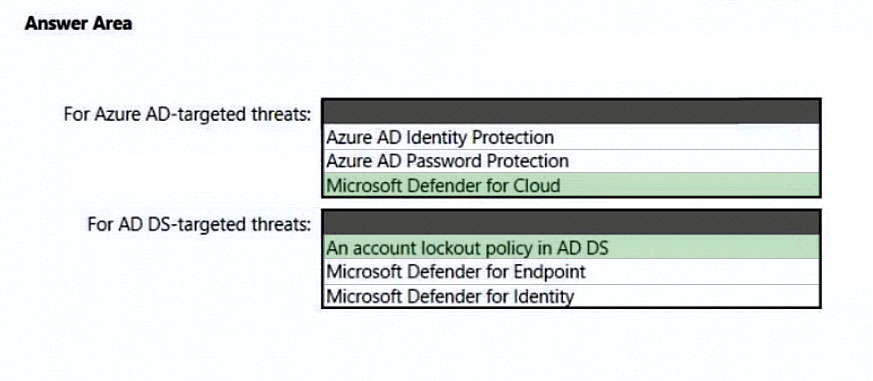
Box 1: Microsoft defender for cloud
Scenario: Prevent AD DS user accounts from being locked out by brute force attacks that target Azure AD user accounts.
When Microsoft Defender for Cloud detects a Brute-force attack, it triggers an alert to bring you awareness that a brute force attack took place. The automation uses this alert as a trigger to block the traffic of the IP by creating a security rule in the NSG attached to the VM to deny inbound traffic from the IP addresses attached to the alert. In the alerts of this type, you can find the attacking IP address appearing in the 'entities' field of the alert.
Box 2: An account lockout policy in AD DS
Scenario:
Detect brute force attacks that directly target AD DS user accounts.
Smart lockout helps lock out bad actors that try to guess your users' passwords or use brute-force methods to get in. Smart lockout can recognize sign-ins that come from valid users and treat them differently than ones of attackers and other unknown sources. Attackers get locked out, while your users continue to access their accounts and be productive.
Verify on-premises account lockout policy
To verify your on-premises AD DS account lockout policy, complete the following steps from a domain-joined system with administrator privileges:
1. Open the Group Policy Management tool.
2. Edit the group policy that includes your organization's account lockout policy, such as, the Default Domain Policy.
3. Browse to Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Account Lockout Policy.
4. Verify your Account lockout threshold and Reset account lockout counter after values.
Reference:
https://techcommunity.microsoft.com/t5/microsoft-defender-for-cloud/automation-to-block-brute-force-attacked-ip-detected-by/ba-p/1616825 https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-password-smart-lockout#verify-on-premises-account-lockout-policy