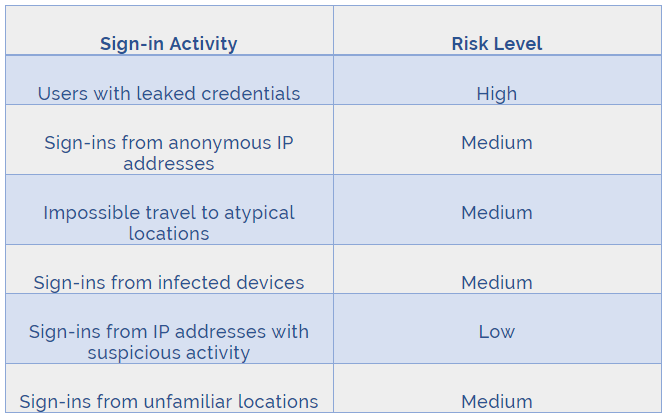
The risk level that should be configured for users that have leaked credentials in a conditional access policy is High.
When a user's credentials are leaked, it means that their username and password have been compromised and are potentially in the hands of an attacker. This puts the user's account and the resources that they have access to at a high level of risk, making it important to apply strict access controls and security measures.
By setting the risk level to High, conditional access policies can be configured to enforce stricter security measures, such as requiring multifactor authentication or blocking access to certain resources entirely.
Therefore, the correct answer is D. High.