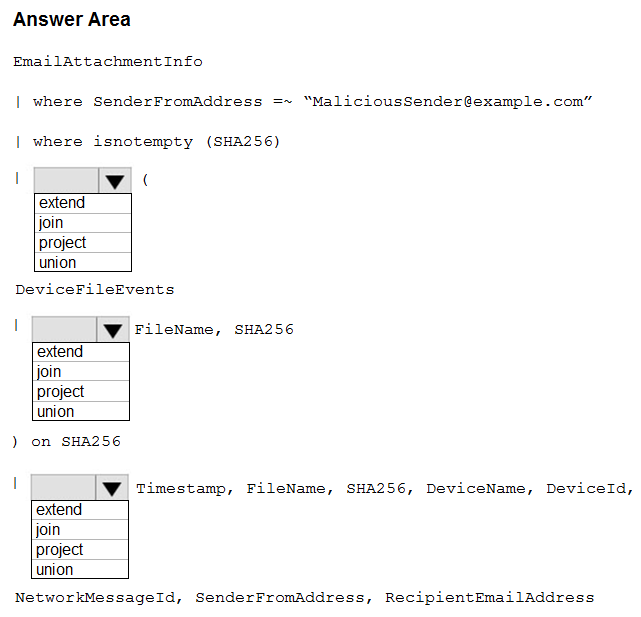
The query posted on MS docs doesnt actually work (I have tested in a live tenant) - it needs to be amended to match the below before it returns results (note the requirement to add DeviceName, and DeviceId fields to the first project statement).
EmailAttachmentInfo
| where SenderFromAddress =~ "<a href="/cdn-cgi/l/email-protection" class="__cf_email__" data-cfemail="24494745574041494b644e514a4b0a474b49">[email protected]</a>"
| where isnotempty(SHA256)
| join (
DeviceFileEvents
| project FileName, SHA256, DeviceName, DeviceId
) on SHA256
| project Timestamp, FileName , SHA256, DeviceName, DeviceId, NetworkMessageId, SenderFromAddress, RecipientEmailAddress
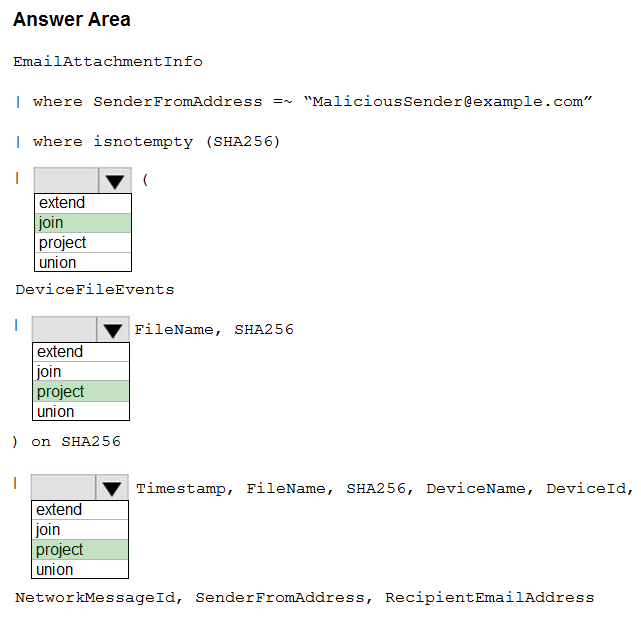
But if you choose the following from the answers presented in the question you will get the results you need to answer the question:
EmailAttachmentInfo
| where SenderFromAddress =~ "<a href="/cdn-cgi/l/email-protection" class="__cf_email__" data-cfemail="89e4eae8faedece4e6c9e3fce7e6a7eae6e4">[email protected]</a>"
| where isnotempty(SHA256)
| join (
DeviceFileEvents
| extend FileName, SHA256
) on SHA256
| project Timestamp, FileName, SHA256, DeviceName, DeviceId, NetworkMessageId, SenderFromAddress, RecipientEmailAddress
ie Choose, Join, Extend, Project from the drop downs
This has also been tested on live tenants and returns the correct result.