You have an Azure subscription that contains the resources shown in the following table.
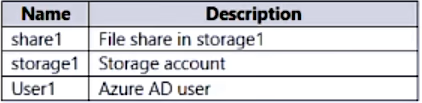
You need to assign User1 the Storage File Data SMB Share Contributor role for share1.
What should you do first?
You have an Azure subscription that contains the resources shown in the following table.

You need to assign User1 the Storage File Data SMB Share Contributor role for share1.
What should you do first?
To allocate the Storage File Data SMB Share Contributor role to User1 for share1, the initial step is to authorize identity-based data access for the file shares in storage1. This action guarantees that individual user access is properly authenticated, adhering to Azure's security protocols. Subsequent to this, you can proceed to configure Access control (IAM) to assign the specific role to User1.
It should be A, I just created a storage account, then created a file share, went to IAM, and it says : To give individual accounts access to the file share (Kerberos), enable identity-based authentication for the storage account.
A is correct I am getting the same message when I go to IAM on File Share. 'To give individual accounts access to the file share (Kerberos), enable identity-based authentication for the storage account'
Correct. Did the same. Very tricky. But this is the right answer.
but its not asking how to give access, its asking what to do first. So dont you need to configure the access control before enabling identity-based data access for the file shares in storage1?
https://learn.microsoft.com/en-us/azure/storage/files/storage-files-active-directory-overview How it works Azure file shares use the Kerberos protocol to authenticate with an AD source. You can enable identity-based authentication on your new and existing storage accounts using one of three AD sources: AD DS, Azure AD DS, or Azure AD Kerberos (hybrid identities only). Only one AD source can be used for file access authentication on the storage account, which applies to all file shares in the account. Before you can enable identity-based authentication on your storage account, you must first set up your domain environment.
Correct. Did the same. Very tricky. But this is the right answer.
but its not asking how to give access, its asking what to do first. So dont you need to configure the access control before enabling identity-based data access for the file shares in storage1?
That is so weird, as I just labbed it. For me answer D As I did just lab it, and I can assign the mentioned role straight out of the box
I also thought it was A. Then I freaked and started doubting when I saw the Vote Distribution being 50-50 between A & D. Thanks for testing and confirming for us. Correct answer should be A then!
Still in 2024, is A correct 3. In the File share settings section, select Identity-based access: Not configured. 4. Under Microsoft Entra Domain Services select Set up, then enable the feature by ticking the checkbox. https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-auth-domain-services-enable?tabs=azure-portal#enable-microsoft-entra-domain-services-authentication-for-your-account
After arguing with ChatGPT here is the answer: The correct steps to assign User1 the Storage File Data SMB Share Contributor role for share1 are: 1. Enable identity-based data access for the file shares in storage1. 2. Configure Access control (IAM) for share1 and add User1 as a role assignment with the Storage File Data SMB Share Contributor role. So the correct answer is A.
kkkkkkkkkkkkkkkk
lol you cant trust ChatGPT to be truthful.
Tested - Was able to assign the role in Access Control (IAM) without enabling identity-based authentication.
D. Configure Access control (IAM) for share1. To assign an Azure role to an Azure AD identity, using the Azure portal, follow these steps: In the Azure portal, go to your file share, or create a file share. Select Access Control (IAM). Select Add a role assignment In the Add role assignment blade, select the appropriate built-in role from the Role list. Storage File Data SMB Share Reader Storage File Data SMB Share Contributor Storage File Data SMB Share Elevated Contributor Leave Assign access to at the default setting: Azure AD user, group, or service principal. Select the target Azure AD identity by name or email address. The selected Azure AD identity must be a hybrid identity and cannot be a cloud only identity. This means that the same identity is also represented in AD DS. Select Save to complete the role assignment operation. https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-ad-ds-assign-permissions?tabs=azure-portal
Tested in lab. Created StorageAccount-->Created File Share1--->Went to IAM of Share1-->Assigned the aforementioned Role to a user--> Done
To assign an Azure AD user a specific role for a file share in Azure Storage, you need to enable Azure Active Directory (Azure AD) authentication over Server Message Block (SMB) for that storage account. This is part of the identity-based access control for Azure file shares. Therefore, the correct first step is: A. Enable identity-based data access for the file shares in storage1.
D. Configure Access control (IAM) for share1. Here’s why: Configure Access control (IAM): In Azure, roles such as the Storage File Data SMB Share Contributor are assigned through the Access control (IAM) settings. This process involves selecting the appropriate role and assigning it to a user or group for a specific resource, which in this case is the file share named share1.
It should be D. In the lab, I created following : 1. A user 2. A new storage account 3. A new file share. Then, I went to file share > IAM > Add role assignment > Members > (newly created user) > Role > (search for given role) > select > review+assign > done. No error, nothing.
Correct Answer: D refer link: https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-ad-ds-assign-permissions?tabs=azure-portal
I'm sorry if I'm misunderstanding the article, but I believe that the correct answer is" C. Select Default to Azure Active Directory authorization in the Azure portal for storage1." The opening lines of the article you linked read "Once you've enabled an Active Directory (AD) source for your storage account, you must configure share-level permissions in order to get access to your file share. There are two ways you can assign share-level permissions. You can assign them to specific Azure AD users/groups, and you can assign them to all authenticated identities as a default share-level permission."
The first line of the section for assigning specific Azure AD users/groups (https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-ad-ds-assign-permissions?tabs=azure-portal#share-level-permissions-for-specific-azure-ad-users-or-groups) states that "If you intend to use a specific Azure AD user or group to access Azure file share resources, that identity must be a hybrid identity that exists in both on-premises AD DS and Azure AD." This is re-iterated in step 5 of the directions to enable this action in the Azure portal: 5. Leave Assign access to at the default setting: Azure AD user, group, or service principal. Select the target Azure AD identity by name or email address. The selected Azure AD identity must be a hybrid identity and cannot be a cloud only identity. This means that the same identity is also represented in AD DS. There is nothing to suggest that the user is a hybrid user so this method would not be an option.
This leaves us with share-level permissions for all authenticated identities, and ss shown in Step 2 here: https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-ad-ds-assign-permissions?tabs=azure-portal#share-level-permissions-for-all-authenticated-identities you must have enabled an AD source on your storage accounts before assigning default share-level permissions.
The first line of the section for assigning specific Azure AD users/groups (https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-ad-ds-assign-permissions?tabs=azure-portal#share-level-permissions-for-specific-azure-ad-users-or-groups) states that "If you intend to use a specific Azure AD user or group to access Azure file share resources, that identity must be a hybrid identity that exists in both on-premises AD DS and Azure AD." This is re-iterated in step 5 of the directions to enable this action in the Azure portal: 5. Leave Assign access to at the default setting: Azure AD user, group, or service principal. Select the target Azure AD identity by name or email address. The selected Azure AD identity must be a hybrid identity and cannot be a cloud only identity. This means that the same identity is also represented in AD DS. There is nothing to suggest that the user is a hybrid user so this method would not be an option.
This leaves us with share-level permissions for all authenticated identities, and ss shown in Step 2 here: https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-ad-ds-assign-permissions?tabs=azure-portal#share-level-permissions-for-all-authenticated-identities you must have enabled an AD source on your storage accounts before assigning default share-level permissions.
https://learn.microsoft.com/en-us/azure/storage/files/storage-files-active-directory-overview File shares can only authenticate using Kerbros token. You must enable identity-based authN - for instance, if you only need cloud-only file share access, you can enable Azure ADDS authN
Who else is confused on this one? I think correct answer is: D. Configure Access control (IAM) for share1. To assign User1 the Storage File Data SMB Share Contributor role for share1, we need to configure Access control (IAM) for share1. This will allow us to add User1 as a member with the required role to manage share1. Option A, enabling identity-based data access for file shares in storage1, is not relevant to the task at hand as we only need to grant a role to User1 for share1. Option B, modifying the security profile for the file shares in storage1, is not a valid action for assigning roles to users. Option C, selecting Default to Azure Active Directory authorization in the Azure portal for storage1, is not related to the task at hand as we need to assign a role to User1 for share1, not change the authentication method for storage1.
It asks what you should do FIRST. And FIRST you must enable the Identity based access and only then add it via IAM.
If you had sourced this that would have been awesome...
Correct Answer: D... To assign an Azure role to an Azure AD identity, using the Azure portal, follow these steps: 1. In the Azure portal, go to your file share, or Create a file share. 2. Select Access Control (IAM). 3. Select Add a role assignment 4. In the Add role assignment blade, select the appropriate built-in role (Storage File Data SMB Share Reader, Storage File Data SMB Share Contributor) from the Role list. Leave Assign access to at the default setting: Azure AD user, group, or service principal. Select the target Azure AD identity by name or email address. 5. Select Review + assign to complete the role assignment operation. https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-auth-active-directory-domain-service-enable?tabs=azure-portal
First thing you need to do is Enable identity based authentication for the storage account
I agree with D, I just tested in my lab as well. Created a storage account, created a file share, left all defaults in place. I was able to use IAM to grant access to User1 straight away without anything else needed. I then proceeded to create a secondary storage account with different settings like the most basic SKUs I could find, and I was still able to assign access via IAM directly.
"You need to assign User1 the Storage File Data SMB Share Contributor role for share1". For him to be able to access the share using his Azure AD account (not via access keys) there is indeed a need to enable Identity Based Data Access. But do I care about that? I just need to grant him the role for share1, which I can clearly do straight away.
.... i had no issues assigning Storage File Data SMB Share Contributor role through IAM to a single user.............. didnt have to do anything else like enable identy based authentication. etc.
Me too, tested in the lab. There were no errors. Straight up add role assignment to the user through IAM.
To assign the SMB Share Contributor role to user1 for Share1, you can follow these steps1: 1. Go to the Azure portal: Log in to your Azure portal. 2. Navigate to the storage account: Browse to the storage account (storage1) that contains the file share (Share1) you created previously1. 3. Select Access Control (IAM): This is where you can manage access to your resources1. 4. Add a role assignment: Select ‘+ Add’, then select ‘Add role assignment’ from the drop-down menu1. 5. Select the role and assign it to the user: In the ‘Add role assignment’ blade, select the ‘Storage File Data SMB Share Contributor’ role from the Role list1. Then, in the ‘Select members’ field, search for and select user11. 6. Review and assign: Review the role assignment details and then click 'Assign’1.
Portal: Fileshare1>Access Control (IAM)>Add a role assignment> Select appropriate built-in role :=> Select Identity target (user/group/principal) Az-CLI: az role assignment create --role "<role-name>" --assignee <user-principal-name> --scope "/../../..fileshares/<share-name>"
When we navigate to file share under storage account > IAM -> It says the following "Identity-based authentication (Active Directory) for Azure file shares To give individual accounts access to the file share (Kerberos), enable identity-based authentication for the storage account."
A seems correct. https://learn.microsoft.com/en-us/azure/machine-learning/v1/how-to-identity-based-data-access?view=azureml-api-1
I toothink D
agree with D , trying to grand access with IAM and worked for me with out first enabling first enabling identity-based authentication for the storage account.
Tested it myself.
I asked Bing AI and this is the answer: To assign the Storage File Data SMB Share Contributor role to User1 for share1, you should follow these steps: 1. In the Azure portal, navigate to your file share or create a new one. 2. Select Access Control (IAM). 3. Click on Add a role assignment. 4. In the Add role assignment blade, select the appropriate built-in role from the Role list: Storage File Data SMB Share Contributor. 5. Leave the Assign access to at the default setting: Azure AD user, group, or service principal. 6. Select the target Azure AD identity representing User1. Here is the link to MS docs: https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-ad-ds-assign-permissions?tabs=azure-portal#share-level-permissions-for-specific-azure-ad-users-or-groups
configuring Access control (IAM) for the specific share (Option D). This allows you to manage access to Azure resources by assigning roles to users, groups, service principals, or managed identities at a particular scope.
Tested assigning Data SMB Share Contributor in IAM
Trust me, I got 900 score mark on recent exam
Trust me bro
hi do you have the contributor access . kindly help with the vrest questions pls
Correct answer is D, the question is here about granting RBAC role to a user. the option A, i about identity based access, it is only needed when you want to give permissions to a file share to lets say end users. It has nothing to do with RBAC role .
To add RBAC role you just need to assign the role to any Entra user through IAM Kerberos access is a different topic don't confuse this with RBAC
I just tried in my account. I have no problems adding a user to the file share, using IAM. However, if I want to connect to this file share, I have two authentication choices: AD and Storage Account Key. If I want to use AD, then I get the "Identity-based access is not configured for this storage account" message. However, the question does not ask about access. We need to add a user to the specific role for the file share. I think D is totally correct in this case.
After reading the link below I think the answer is A. See the section: "To assign an Azure role to an Azure AD identity, using the Azure portal, follow these steps" https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-ad-ds-assign-permissions?tabs=azure-portal
The answer is D. You have to click "Access control (IAM)" FIRST before you can add the Storage File Data SMB Share Contributor role.
No, option D mentions Configure Access control (IAM) for "share1". What you need to configure first is the storage account "storage 1". So option D cannot be correct.
It is configured for the specific file share, not the storage account "Share-level permissions for specific Microsoft Entra users or groups 1. In the Azure portal, go to your file share, or create a file share. 2. Select Access Control (IAM). 3. Select Add a role assignment 4. In the Add role assignment blade, select the appropriate built-in role from the Role list. Storage File Data SMB Share Reader Storage File Data SMB Share Contributor Storage File Data SMB Share Elevated Contributor 5. Leave Assign access to at the default setting: Microsoft Entra user, group, or service principal. Select the target Microsoft Entra identity by name or email address. The selected Microsoft Entra identity must be a hybrid identity and cannot be a cloud only identity. This means that the same identity is also represented in AD DS. 6. Select Save to complete the role assignment operation." https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-ad-ds-assign-permissions?tabs=azure-portal#share-level-permissions-for-specific-microsoft-entra-users-or-groups
Before you can give user accounts access to the SHARE, you need to enable this feature on the STORAGE ACCOUNT that includes this share. So option A is correct. Option D is clearly wrong.
To give individual accounts access to the file share (Kerberos), enable identity-based authentication for the storage account.
Should B a as it needs UDentity-based authentication for individual users
I think I'm going to go with A based on the following information I found when I search the differences between identity-based access and access control IAM: Identity and Access Management (IAM) IAM is a cybersecurity discipline that manages how users access digital resources and what they can do with them. IAM systems verify users' identities and ensure that they have the correct permissions to do their jobs. IAM can also integrate with AI-based cybersecurity tools to analyze data for potential cyber attacks. Access control Access control is a data security process that manages who has access to corporate data and resources. Access control uses policies to verify users' identities and grant them the appropriate level of access. Access control is important for applications that have different levels of authorization for different users.
To assign User1 the Storage File Data SMB Share Contributor role for share1 (a file share in storage1), you first need to enable identity-based data access for file shares in storage1. This is required so that you can use Azure AD-based authentication for accessing the file shares. Once identity-based access is enabled, Azure Active Directory (Azure AD) users like User1 can be assigned roles such as Storage File Data SMB Share Contributor to control access to Azure file shares. You will eventually need to assign the role to User1 using IAM, but first, you must enable identity-based access to the file shares.
Correct answer is D I tried the same way like macrawat however in my case that works - inside created file share "share1" I was able to grant access from IAM to user. State of identity-based access is "not configured" as on screenshot from microsoft doc https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-auth-domain-services-enable?tabs=azure-portal
Really? see the documentation that you sent, what's the first thing being configured?
Today, Feb 2025, you i could add Storage File Data SMB Share Contributor role for a user without enable identity-based data access for the file shares in storage1. D is correct
D is ok tested with a pay as you go
Selected Answer: B
To assign User1 the Storage File Data SMB Share Contributor role for share1, you should first configure Access control (IAM) for share1. Access control (IAM) allows you to manage access to Azure resources by assigning roles to users, groups, or applications. By configuring Access control (IAM) for share1, you can grant User1 the necessary role to manage the storage file data SMB share. Therefore, the correct option is: D. Configure Access control (IAM) for share1.
D. as per Chat GPT
D is correct per checked. I never met the identity-based alert when I authorize an AAD user, someone know why?
I know the answer is exactly D. identity-based authentication is used for LOCAL AD OR HYBRID AD
The answer is not “D. Configure Access control (IAM) for share1” because before you can use Azure role-based access control (Azure RBAC) to manage access to the file shares in storage1, you must first enable identity-based data access for the file shares in storage1. This is done by selecting Default to Azure Active Directory authorization in the Azure portal for storage1. Once identity-based data access is enabled, you can then use Azure RBAC to assign roles such as the Storage File Data SMB Share Contributor role to users for share1 by configuring Access control (IAM) for share1.
Without doing any steps I was able to add the user This is what I see in the notifications Added Role assignment azureadsql was added as Storage File Data SMB Share Contributor for eu100320029be0bd3a. Answer is D
Under configuration of my storage account the Default to Azure Active Directory authorization in the Azure portal is Disabled One more proof Answer is D IAM
Azure AD user
D. Setup a file share, and then go to IAM and assign the user the role.
Can it depend on the current authentication method?? If we assume that you're authenticating using your Microsoft Entra account them D?? https://learn.microsoft.com/en-us/azure/storage/files/authorize-data-operations-portal#specify-how-to-authorize-operations-on-a-specific-file-share
The correct answer is D. You cannot enable identity-based data access for file shares in a storage account until the IAM has already been configured.
The first step is A and ssecond step is D. since the question is about what should you do first? Answer is A
A is correct
Correct Answer is A. tested as well.
A is right
Option C: Select Default to Azure Active Directory authorization in the Azure portal for storage1 - This option is the most straightforward and necessary initial step for setting up Azure AD-based authorization. It directly configures the storage account to use Azure AD for access control, which is a prerequisite for assigning Azure AD roles to manage access to file shares.
A is correct key words are what should you do first, A is done first before D.
A. Enable identity-based data access for the file shares in storage1
chatgpt To assign User1 the Storage File Data SMB Share Contributor role for share1, the first step is to ensure that Azure Active Directory (AD)-based authentication is enabled for the file shares. This allows Azure AD users to be authenticated when accessing the file shares using SMB. In this scenario, the correct action to perform first is: A. Enable identity-based data access for the file shares in storage1. Explanation: Azure Files supports Azure AD-based access control for file shares using SMB. However, before you can assign roles like Storage File Data SMB Share Contributor, you need to enable identity-based access for the file shares within the storage account (storage1 in this case). Once identity-based access is enabled, you can then assign roles such as Storage File Data SMB Share Contributor to Azure AD users like User1, granting them the necessary permissions on share1.
I prefer A then D
Should be A enable identity-based authentication 1st, then only go to D, IAM
The answer is A
Definetly A is the correct answer. That is the first step.
A for me is correct
Just repro in a lab with a new storage account. Identity-based access can be enabled in two steps for a particular share in this storage account. This allows individual users to use their Active Directory or Microsoft Entra account to gain access to a specific file share. Step 1: Enable an identity source
By the way - If I need wait for moderator approval my comment. Why comments with wrong answers are visible? I see a lot of new comments (1-6 months ago) "YEA I HAD A CHAT WITH CHAT GPT THE ANSWER IS 100% A" - Hollllyyy and the price is higher and higher....
Just tested it, create storage, selected IAM and gave the user the role.
Tested and "Identity-based access: Not configured"
The correct answer is A. Enable identity-based data access for the file shares in Storage1 Enable identity-based data access for the file shares in Storage1: This step is necessary to allow Azure AD identities to access the file shares. Without enabling identity-based data access, you cannot assign Azure AD roles like the Storage File Data SMB Share Contributor role to users for accessing file shares.
Modify the security profile for the file shares in Storage1: This option is not relevant to the task. Modifying the security profile does not enable identity-based access or allow role assignments. Security profiles typically involve settings related to encryption, access protocols, and other security configurations. Select Default to Azure Active Directory authorization in the Azure portal for Storage1: While this option is related to enabling Azure AD authorization, it is not the first step. You need to enable identity-based data access first before you can configure Azure AD authorization settings.
https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-assign-share-level-permissions?tabs=azure-portal To assign an Azure role to a Microsoft Entra identity, using the Azure portal, follow these steps: 1. In the Azure portal, go to your file share, or create an SMB file share. 2. Select Access Control (IAM). 3. Select Add a role assignment 4. In the Add role assignment blade, select the appropriate built-in role from the Role list. 5. Leave Assign access to at the default setting: Microsoft Entra user, group, or service principal. Select the target Microsoft Entra identity by name or email address. The selected Microsoft Entra identity must be a hybrid identity and cannot be a cloud only identity. This means that the same identity is also represented in AD DS. 6. Select Save to complete the role assignment operation.