AC
A: When a client acquires an access token to access a protected resource, the client also receives a refresh token. The refresh token is used to obtain new access/refresh token pairs when the current access token expires. Refresh tokens are also used to acquire extra access tokens for other resources.
Refresh token expiration -
Refresh tokens can be revoked at any time, because of timeouts and revocations.
C: Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. It uses a combination of endpoint behavioral sensors, cloud security analytics, and threat intelligence.
The interviewees said that ג€by implementing Zero Trust architecture, their organizations improved employee experience (EX) and increased productivity.ג€ They also noted, ג€increased device performance and stability by managing all of their endpoints with Microsoft Endpoint Manager.ג€ This had a bonus effect of reducing the number of agents installed on a user's device, thereby increasing device stability and performance. ג€For some organizations, this can reduce boot times from
30 minutes to less than a minute,ג€ the study states. Moreover, shifting to Zero Trust moved the burden of security away from users. Implementing single sign-on
(SSO), multifactor authentication (MFA), leveraging passwordless authentication, and eliminating VPN clients all further reduced friction and improved user productivity.
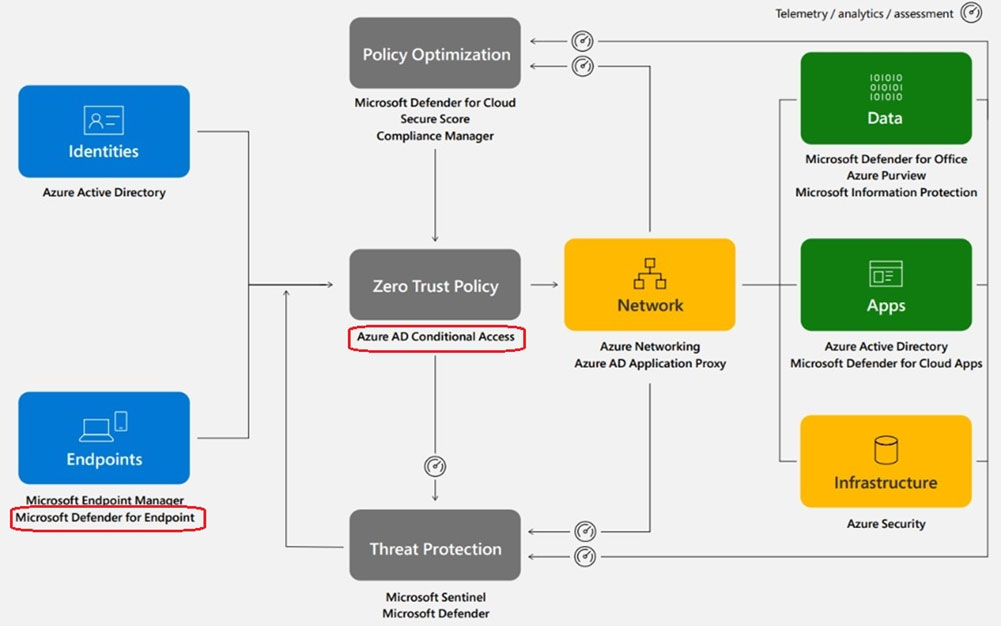
Note: Azure AD at the heart of your Zero Trust strategy
Azure AD provides critical functionality for your Zero Trust strategy. It enables strong authentication, a point of integration for device security, and the core of your user-centric policies to guarantee least-privileged access. Azure AD's Conditional Access capabilities are the policy decision point for access to resource
Reference:
https://www.microsoft.com/security/blog/2022/02/17/4-best-practices-to-implement-a-comprehensive-zero-trust-security-approach/ https://docs.microsoft.com/en-us/azure/active-directory/develop/refresh-tokens
