HOTSPOT -
You implement the planned changes for NSG1 and NSG2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
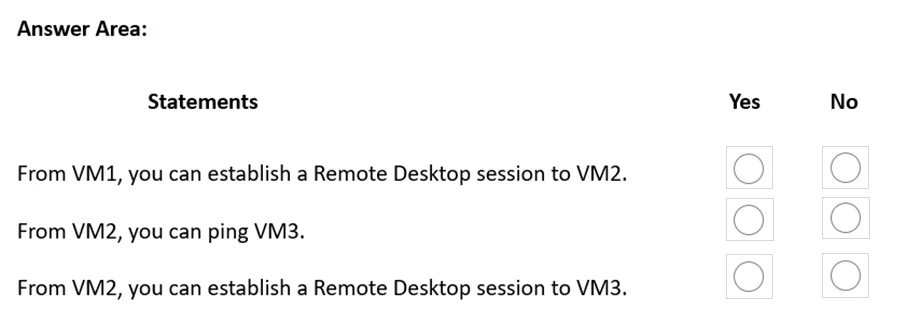
HOTSPOT -
You implement the planned changes for NSG1 and NSG2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

I think the Answers should be: YYN VM1 has inbound rules, so no restriction on outbound. VM2 has outbound rules, so no restrictions on inbound. Hence VM1 can establish RDP to VM2. VM2 —ping—> VM3: Yes(no restriction other than outbound RDP) VM2 —RDP—> VM3: No(outbound RDP is not allowed on VM2) Please correct me if I am wrong. Tmrw I have my exam.
Passed the exam today with 920/1000. This case was not there in my exam.
how do you say it's one outbound rule for the VM2? NSG2 source for the rdp deny rule is a 10.0.0.0/16 and the ip of the VM1 is on this subnet. I think that is NYN the answer
I thought the same thing at first, and had to read it three times before I noticed what I was missing. Create an NSG named NSG1 that will have the custom INBOUND security rules shown in the following table. Create an NSG named NSG2 that will have the custom OUTBOUND security rules shown in the following table. Capitalized for emphasis. It's YYN.
Thank you! Didn't spot the inbound and outbound wording. Agree Y,Y,N
Thank you! Didn't spot the inbound and outbound wording. Agree Y,Y,N
I agree that is YYN: 1-The rule is configured inbound from VM1 and VM2 will allow the traffic because of stateful firewall inspection, the traffic is allowed to come in. If the traffic is initiated from VM2 them it wouldn't work. 2-ping will be allow because the vnets are already peered 3-No, traffic is initiated from VM2 and the outbound rule will block it. Feel free to correct me if I am wrong.
I thought the same thing at first, and had to read it three times before I noticed what I was missing. Create an NSG named NSG1 that will have the custom INBOUND security rules shown in the following table. Create an NSG named NSG2 that will have the custom OUTBOUND security rules shown in the following table. Capitalized for emphasis. It's YYN.
Thank you! Didn't spot the inbound and outbound wording. Agree Y,Y,N
Answer valid! This question was on the exam 22/02/2023. Scored 920.
Thank you! Didn't spot the inbound and outbound wording. Agree Y,Y,N
Ill say Y Y Y Vnet 2 and 3 are peered so NGS shouldnt consider them different Vnet to apply restrictions unless you block the traffic https://blog.aelterman.com/2021/01/08/defaulting-azure-virtual-network-peering-from-allowing-to-denying-traffic/
Last one is N. RDP traffic will be dropped by NSG2 rule #200. 'VirtualNetwork' service tag includes all peered vnet's address spaces. https://learn.microsoft.com/en-us/azure/virtual-network/service-tags-overview
No NSG2 explicitly denies outbound RDP traffic from VM1 to VM2. Even if NSG1 allowed inbound RDP, NSG2 would still block it. NSG2 explicitly denies outbound RDP traffic from VM1 to VM2. Even if NSG1 allowed inbound RDP, NSG2 would still block it.
NGS2 is applied to Vnet1/Subnet2 outbound. I think you've confused yourself with direction of traffic flow.
NGS2 is applied to Vnet1/Subnet2 outbound. I think you've confused yourself with direction of traffic flow.
Last one is N. RDP traffic will be dropped by NSG2 rule #200. 'VirtualNetwork' service tag includes all peered vnet's address spaces. https://learn.microsoft.com/en-us/azure/virtual-network/service-tags-overview
From VM1, you can Esablish a Remote Desktop sesion to VM2: Yes They are in the same subnet and VM1 doesn't have restriction on outbound and VM2 doesn't have restriction on inbound From VM2, you can ping VM3: No Rule 400 only permit ping from 10.0.2.0/24 to 10.0.1.0/24. VM3 has 172.16.1.4 IP address From VM2, you can establish a Remote Desktop sesion to VM3: No Rule 200 only permit virtualNetwork (VNET1) destination RDP and VM3 is in VirtualNetwork VNET2
Sorry, I made a mistake in the explanation: From VM2, you can establish a Remote Desktop sesion to VM3: No Rule 200 blocks RDP traffic
Sorry I can't update the answer and I have to make a new post: Finaly I think is : YYN From VM1, you can Esablish a Remote Desktop sesion to VM2: Yes They are in the same VNET and VM1 doesn't have restriction on outbound and VM2 doesn't have restriction on inbound From VM2, you can ping VM3: Yes Rule 400 only permit ping from 10.0.2.0/24 to 10.0.1.0/24. VM3 has 172.16.1.4 IP address, but there are implicit rules: any(port) any(protocol) virtualnetwork(source) to virtualnetwork (destination). The VNETs are peered and ping works. From VM2, you can establish a Remote Desktop sesion to VM3: No Rule 200 blocks RDP traffic
Sorry I can't update the answer and I have to make a new post: Finaly I think is : YYN From VM1, you can Esablish a Remote Desktop sesion to VM2: Yes They are in the same VNET and VM1 doesn't have restriction on outbound and VM2 doesn't have restriction on inbound From VM2, you can ping VM3: Yes Rule 400 only permit ping from 10.0.2.0/24 to 10.0.1.0/24. VM3 has 172.16.1.4 IP address, but there are implicit rules: any(port) any(protocol) virtualnetwork(source) to virtualnetwork (destination). The VNETs are peered and ping works. From VM2, you can establish a Remote Desktop sesion to VM3: No Rule 200 blocks RDP traffic
VM1 - VNET1/Subnet1 - Inbound rules - No outbound rules VM2 - VNET1/Subnet2 - Outbound rules - No inbound rules VM3 - VNET2/Subnet1 Box1 - YES VM1 no outbound rules VM2 no Inbound rules. same VNET, subnet to subnet Allowed by default. Box2 - NO VM2 has outbound ICMP rule to Allow from 10.0.2.0/24 to 10.0.1.0/24 only. VM3 is 172.16.1.4 but VNET1 and VNET2 are peered which means inbound traffic between subnets has not restriction. Box3 - NO VM2 has outbound RDP rule to Deny from 10.0.0.0/16 to any VNET.
I mean Box2 is YES. sorry.
I think the answer is NYN. 1. VM1 will try to connect with VM2 but the VM2 have default inbound rules and by default port 3389 is blocked. For, this to happen VM2 has to have inbound security rule that opens port 3389. 2. Yes : the VNET2 and VNET3 are peered. 3. No: Outbound RDP not allowed on VM2
NO - Rule 200 outbound for VNET1/Subent2 and Rule 500 for Income from VNET1/Subent2(10.0.2.0/24) deny the traffic through port3389. VM1 don't have restriction to request on port 3389 to Subnet2 VM2, but VM2 when response on this request from VM1 on 3389 RULE 200 in NSG2 will deny this message from VM2 response YES - VNET1 and VNET2 are peered and default 65000 Rule AllowVnetOutBound allow any protocol and any port. Keep in mind default rules existing in NSG NO Rule 200 Deny
Y: same VNET, no restriction N: VMs are not in the same VNET and not peered N: VMs are not in the same VNET and not peered
they are peered ... look at the able above
No: Traffic is allowed from NSG1 but blocked by NSG2 VM1-->--NGS1--X--NSG2----VM2 Yes: No rules applied; networks are peered VM2-->--NSG2-->--VM3 No: NSG2 blocks traffic by the very same rule tha blocks from VM1 (same ip range) VM2--X--NSG2----VM3
VM1/VNET1/SUBNET1/10.0.1.4 VM1/NSG1/INBOUND - Deny 3389 from VNET1/SUBNET2 VM1/NSG1/INBOUND - Allow ICMP VM2/VNET1/SUBNET2/10.0.2.4 */VNET1/SUBNET2/NSG2/OUTBOUND - Deny 3389 from 10.0.0.0/16 to vnet */VNET1/SUBNET2/NSG2/OUTBOUND - Allow ICMP from 10.0.2.0/24 to 10.0.1.0/24 VM3/VNET2/SUBNET1/172.16.1.4 (VNET2 peered to VNET1, VNET3) From VM1, you can establish a Remote Desktop session to VM2 Yes. Same VNET. NSG1 denys inbound RDP to VM1 AND NSG2 denys outbound RDP from subnet2 From VM2, you can ping VM3 No. NSG2 Default rule DenyAllOutBound blocks VNET1 to VNET2 From VM2, you can establish a Remote Desktop session to VM3 No. NSG2 Default rule DenyAllOutBound blocks VNET1 to VNET3 https://learn.microsoft.com/en-us/azure/virtual-network/network-security-group-how-it-works
i think no, no, no no- RDP protocol , not TCP no- window server by default not allow ping(echo request) https://www.thomasmaurer.ch/2019/09/how-to-enable-ping-icmp-echo-on-an-azure-vm/ no-RDP, not TCP
Came in exam today 5/31/23
1. From VM1, you can establish a Remote Desktop session to VM2. No because NSG2 outbound rule will prevent the RDP connection 2. From VM2, you can ping VM3. Yes because No rules prevent this ping. 3. From VM2, you can establish a Remote Desktop session to VM3. No because NSG2 prevent his RDP connection
"1. From VM1, you can establish a Remote Desktop session to VM2. No because NSG2 outbound rule will prevent the RDP connection" You're wrong! It's only outbound rule attached to Subnet2 (which contains only VM2). So from VM2 this rule indeed would block RDP connection to VM1 (or any other), but from VM1 it doesn't apply, as then it's inbound rule from VM2(subnet2) perspective.
Y - Y - N
N,Y, N
NYN Correct No, if outgoing traffic on port 3389 is blocked, you will not be able to establish an RDP even if the incoming rdp is open in the remote server
This was in Exam 23-08-23
NSG Rules : NSG1 (VM1 Level) vm1 can be pinged by any servers in Vnet vm1 cannot accept RDP from vnet1/subnet2 (vm2) [vm2 to vm1 not possible] --------- NSG2 (Subnet Level ) [10.0.2.0/24] vm2 cannot RDP any server [Source : 10.0.0.0/16] vm2 can ping vm1 ------------- Q1.From VM1 to VM2 (RDP) : No [blocked by NSG2] Q2. VM2 to ping Vm3 : No NSG rule, but 2 different Vnet1 to Vnet2 as per Default NSG Rules : Yes Q3.vm2 to vm3 (RDP) : No [blocked by NSG2] Given Answer is Correct...
Seeing so many conflicting answers, I tested this in my lab. Initially, without testing, my answer was No, Yes, No but I was surprised with the test results. I have basically replicated the scenario given and double checked that everything was configured correctly. Here are the results: - From VM1, I can RDP into VM2 - From VM2, I can ping VM3 (only if I disable Windows Firewall) - not sure what the state of the firewall is on this VM but I assume it's off because the question focuses on the NSG rules and your understanding of them. - From VM2, I can establish a RDP session to VM3. Therefore, I would say the answer is Y, Y, Y.
If you wonder why the NSGs don't apply, is because the traffic is not leaving the VNETs since they are peered, so everything is considered "internal" traffic just like if the VMs were on the same VNET/Subnet. The only point that you can argue is Box2, where if you don't intentionally disable Windows Firewall or allow ICMP on the VM itself, the answer would be NO as ping is blocked by default in Windows Firewall, so you need to take your chances here. Either read the question as if they were testing your understanding of the NSGs and how the rules would apply given the scenario in question, or read it like a sysadmin would and don't make assumptions. For instance, if they don't say Windows Firewall is off on VM3 then assume it's not as the default configuration has all firewall profiles turned on. Y/Y/Y if you make an assumption and turn off Windows Firewall or Y/N/Y if you don't assume anything.
Yes Yes No
Yes Yes No
WRONG Yes Yes No
Hello SeMoOoOoOo I always see you in Examtopics, can you tell where the question is. I just find out the answer.
YES: VM1 => VM2 (RDP connection) NSG1 (inbound rule), hence no restriction YES : VM2 => VM1 (ping) they are peered NO : VM2 => VM3 (RDP connection) NG2 (outbound rule), hence NOT allowed
This question was on the test 11/12/2022: YYN
YNN I dont believe you can ping VM3 from VM2 although they are in a peered network they are windows machines that block ICMP ping, VM3 would require a inbound rule to allow ICMP
NYY Correct No, if outgoing traffic on port 3389 is blocked, you will not be able to establish an RDP even if the incoming rdp is open in the remote server
This is absolutely false, and important to understand. NSG's are stateful in nature. If you are attempting to RDP into a box, and the NSG/inbound rule allows it, you do not need a corresponding outbound rule for 3389, nor will an outbound rule blocking 3389 have any effect. https://stackoverflow.com/questions/73160450/if-azure-network-security-groups-are-stateless-are-outbound-denys-overridden#:~:text=Yes%2C%20Azure%20NSGs%20are%20stateful%20and%20work%20similarly.,is%20initiated%20externally.%20The%20opposite%20is%20also%20true.
Box1 = NO, here's why VM1 cannot connect to VM2. Let's check the data flow rules. Vnet1 and Vnet2 are peered so they can communicate between them. NSG1 is tied to VM1's NIC; NSG1 will block RDP connections attempts originated from [vnet1/subnet2]; that is an inbound rdp block rule on VM1, so nobody from subnet2 can RDP to VM1, however that's not what we are looking for. Now let's check NSG2: it is tied to [vnet1/subnet2] so it applies to VM2. NSG2 is blocking RDP connection attempts orignitated form the whole VNET1 (10.0.0.0/16 includes the following range: 10.0.0.0-->10.0.255.255) so RDP packet will never reach VM2.
In Existing Environment section, it said "No network security groups (NSGs) are associated to the network interfaces or the subnets.". Then, in planned changes section, NSG1 is attached to VM1's NIC and NSG2 is attached to VNET1/Subnet2. Thus, VM3 has no NSG attached to its NIC nor its subnet. There is no single inbound rule allow any traffic. I tested in Lab. From VM2, you can NOT ping VM3 AND you can NOT establish a Remote Desktop session to VM3. So, my answer is YNN.
N - There is an TLS handshaking process to establish an RDP connection between 2 VMs. Both inbound and outbound rules must allow TCP protocol && Port 3389 (default for RDP) to open for both VMs. Inbound itself (or outbound itself) is not enough for the connection because of the handshake steps. Y N
The correct answer with some consideration is YYN Reasons: Q1: As @humnahibataynge mentioned, "VM1 has inbound rules, so no restriction on outbound, and VM2 has outbound rules, so no restrictions on inbound." So we can establish RDP from VM1 to VM2. So YES (TESTED IN LAB) Q2: If we assume that the firewall on both VM2 and VM3 is not blocking ICMP then we can ping VM3 from VM2. Answer would be YES (TESTED IN LAB) Q3: The only reason the makes VM2 not being able to RDP to VM3 is that VM3 does not have any NSG associated with it so literally you can not RDP to VM3 from any source(TESTED IN LAB). The trick here is the destination of the outbound rule in NSG2 is service tag: VirtualNetwork! So only the RDP to any destination inside the vnet(e.g. VM1) will be denied!(TESTED IN LAB) Therefore if we add a proper NSG to VM3 we will be able to RDP to VM3 from VM2! Please correct me if I'm wrong.
Goodluck, Got mine on 5 sep.
Correct answers : YYN
Yes today on my exam. My score was 900
Ans is definately YYN
please lets review this together guys, "Associate NSG1 to the network interface of VM1" which is DENYING inbound traffic for 3389 from VM2. but the question states FROM VM1 --> VM2 . so the NSG1 does not come in play as it is only for INBOUND RDP TRAFFIC TO VM1 not outbound vm YES YES NO - as the outbound traffic is from source 10.0.0.0/16 ( the entire 10.0.255.255, that VM2 fails in) with port 3389 to any VNET
New-NetFirewallRule –DisplayName "Allow ICMPv4-In" –Protocol ICMPv4 this must be entered to allow a VM to ping another VM in a peered network windows firewall blocks ICMP the case study indicates we are using windows machines.
I'd say you are overthinking it. Nothing prevents us from thinking the firewalls are open as needed on the VMs. Here we need to justify ping possibility from NSG configuration stand point. Yes the VM might not return the ping response. But it doesn't mean ping request can't reach the destination.
From VM1, you can establish a Remoted Desktop seddion to VM2 -> NO, If i understand well, the default rule is applied for RDP, correct?
It's YYN. Y,Y,N flurgen248 -> YES!
YYN is correct!
I did the lab and I found: Y,NY And ping to VM3 no work only because Windows Firewall is enable. If you disable windows firewall Ping works.
How do many people know that the vnets are peered? I can't find it in te case text.
Look at 2nd table, the one with the headings of "Name" and "Subnet' and "Peered with"
read full questions at least twice
When there is no restriction means that default it is allowed. https://learn.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview#default-security-rules https://learn.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview#default-security-rules:~:text=You%20can%27t%20remove%20the%20default%20rules%2C%20but%20you%20can%20override%20them%20by%20creating%20rules%20with%20higher%20priorities.
1) From VM1, you can establish a Remote desktop session to VM2? =NO VM2 has the NSG2 applied: Port: 3389 Source: 10.0.0.0/16 (includes 10.0.0.0-10.0.255.55) VM1 IP(10.0.1.4) falls in this range Action: DENY So incoming connections to VM2 from those IP ranges will be BLOCKED
Please correct me if Wrong for Box3- the answer should be YES because the NSG2 rules applied to VM2 states [Action: Deny (So all inbound connections from that IP address range will be denied)]. Additionally VM2 is PEERED with VNET 2- VM3 is on [Connected to: VNET2/Subnet1] 3) From VM2, can you establish a RDP session to VM3? VM2 IPaddress: 10.0.2.4 LOCATIon: West US Connected to: VNET1/Subnet2 **NSG2 Port: 3389(RDP) Source: 10.0.0.0/16 (10.0.0.0-10.0.255.255) Destination: VirtualNetwork (INBOUND connections to virtualNetwork) Action: Deny (So all inbound connections from that IP address range will be denied) Subnet: Subnet1, Subnet2 PEEREDwith: VNET2 — VM3 IPaddress: 172.16.1.4 Location: Central US Connected to: VNET2/Subnet1 Subnet: Subnet1 PEEREDwith: VNET1, VNET3
MS proprietary security rules, when no rules defined, means freely access, not secure by default, thats the resson why MS ptoduct is an easy target.