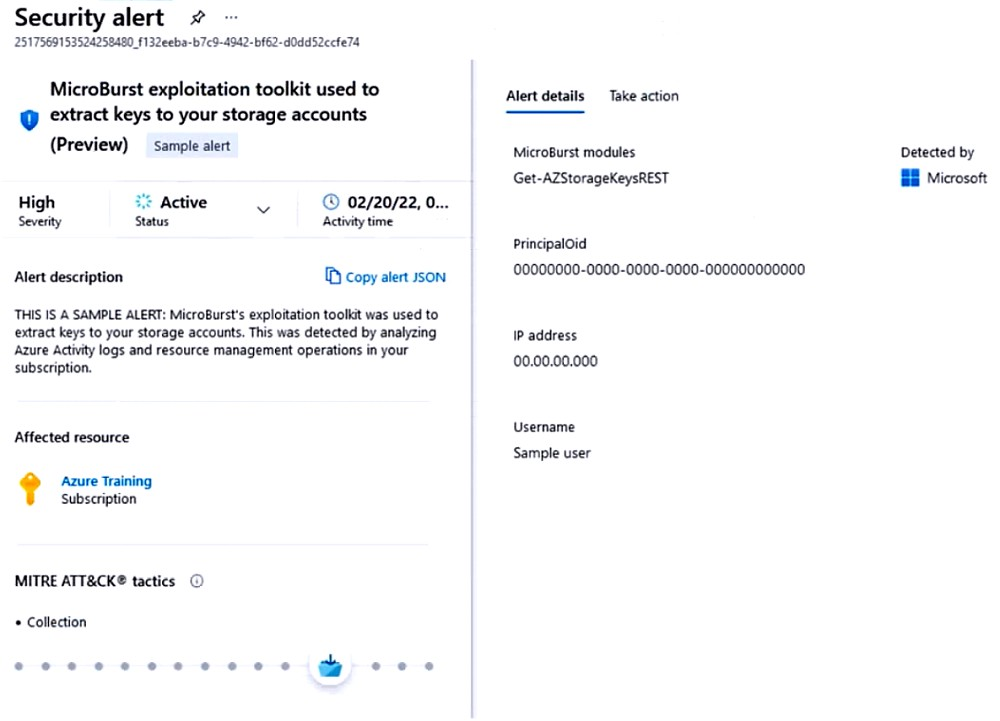
You receive a security alert in Microsoft Defender for Cloud as shown in the exhibit. (Click the Exhibit tab.)
After remediating the threat, which policy definition should you assign to prevent the threat from reoccurring?
You receive a security alert in Microsoft Defender for Cloud as shown in the exhibit. (Click the Exhibit tab.)

After remediating the threat, which policy definition should you assign to prevent the threat from reoccurring?
To prevent a similar threat from reoccurring, you should assign the policy definition that ensures storage accounts prevent shared key access. The MicroBurst exploitation toolkit leverages shared key access to perform its attacks. By disallowing shared key authorization, you ensure that storage accounts are protected from unauthorized key retrieval attempts. Requiring Azure Active Directory credentials for access adds an additional security layer, making it more difficult for attackers to exploit storage accounts using brute-force techniques or other tactics targeting shared keys.
C is the correct answer. You should read Microburst toolkit - it is an open-source tool. Find Get-AZStorageKeysREST.ps1 it tries to enumerate all storage accounts then the respective storage keys. There is nothing to do with anonymous access here. Even if a storage account allows public acces you can't get the key without being authenticated and authorized. The preventive control here is to manage Shared Key Authorization.
I would select "Storage accounts should prevent shared key access"
... by applying read-only lock.
C is the answer. https://learn.microsoft.com/en-us/azure/storage/common/shared-key-authorization-prevent?tabs=portal Every secure request to an Azure Storage account must be authorized. By default, requests can be authorized with either Azure Active Directory (Azure AD) credentials, or by using the account access key for Shared Key authorization. Of these two types of authorization, Azure AD provides superior security and ease of use over Shared Key, and is recommended by Microsoft. To require clients to use Azure AD to authorize requests, you can disallow requests to the storage account that are authorized with Shared Key.
I would go with C as it is not talking about data but keys..Make a Storage Account Public/Private (if it is related network) is use case based and cant be enforced always.. Anonymous access makes sense but that is for the data and the powershell command is trying to extract the access the keys, and not data
Good point - I am going with C
MicroBurst leverages the Get-AZStorageKeysREST.ps1 script to brute-force enumerate storage accounts and subsequently attempt to retrieve their keys using REST API calls. Public access isn't directly targeted by this script. While disallowing public access (option A) is a generally good security practice, it wouldn't specifically prevent the MicroBurst exploitation technique that relies on shared key access. Even with public access blocked, the script could still enumerate accounts and try brute-forcing shared keys. Preventing shared key access (option C) directly addresses the vulnerability exploited by the script. By disabling this access method, storage accounts become protected from unauthorized key retrieval attempts using Get-AZStorageKeysREST.ps1 or similar tools.
"... By default, requests can be authorized with either Azure Active Directory credentials, or by using the account access key for Shared Key authorization. Of these two types of authorization, Azure AD provides superior security and ease of use over Shared Key, and is recommended by Microsoft." https://github.com/Azure/azure-policy/blob/master/built-in-policies/policyDefinitions/Storage/StorageAccountAllowSharedKeyAccess_Audit.json
I agree. C is correct.
My answer would be C. Note that the question is asking "After remediating the threat, which policy definition should you assign to prevent the threat from reoccurring". Answer A mitigate the attack by limiting exploit only thru private network links. However, to entirely prevent threat from re-occuring, simply stop using preShare key authorization.
Not sure how 80% voted for the wrong answer. The correct answer is A. https://hacknowledge.com/blog-post/azure-blob-storage-detect-and-prevent-public-accesses/
The correct is C, see the docs: https://learn.microsoft.com/en-us/azure/defender-for-cloud/alerts-reference
After remediating the threat, to prevent it from reoccurring, you should assign the following policy definition: C. Storage accounts should prevent shared key access This policy ensures that shared keys are not used for access to storage accounts, which aligns with security best practices and helps prevent similar threats in the future .
The Correct Answer is A. According to Microsoft Public storage accounts have a URL of a public endpoint (more information in the Background section), which means that it's possible to guess storage accounts names by performing DNS queries on the URL and examining the response. The way to prevent this is to remove Public access. https://techcommunity.microsoft.com/t5/microsoft-defender-for-cloud/protect-your-storage-resources-against-blob-hunting/ba-p/3735238
I am torn between A and C, in my opinion it should be both that would make sense. I really don't know what to choose for the exam now - A or C.
I vote for C. Azure AD provides superior security and ease of use over Shared Key, and is recommended by Microsoft. here the link: https://learn.microsoft.com/en-us/azure/storage/common/shared-key-authorization-prevent?tabs=portal
Selected Answer: A From the picture above you can see access from IP 0.0.0.0 that means from internet (public access). SAS token allow limited access to storage.
is the right answer
Not sure why preventing shared key access would be better than blocking public access. After all there are far more hackers in the outer world that would rather push an open door than test shared keys. Just my own two pennies
Remember that threats could come from inside, not just outside. That's why C is the right answer. If no key is available, there is nothing to steal.
Option C - When you disallow Shared Key authorization for a storage account, Azure Storage rejects all subsequent requests to that account that are authorized with the account access keys. Only secured requests that are authorized with Microsoft Entra ID will succeed.