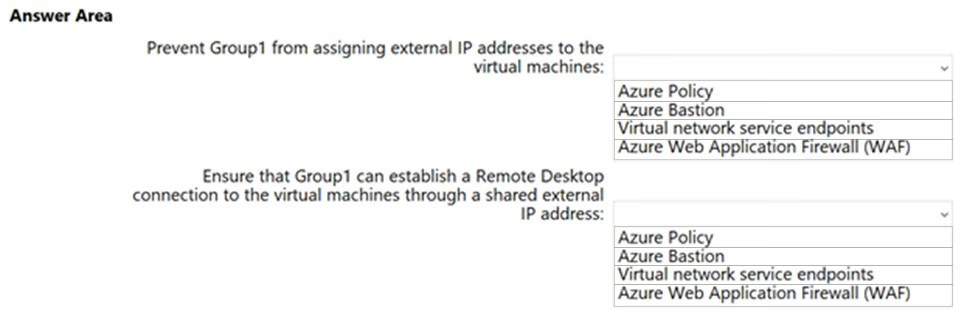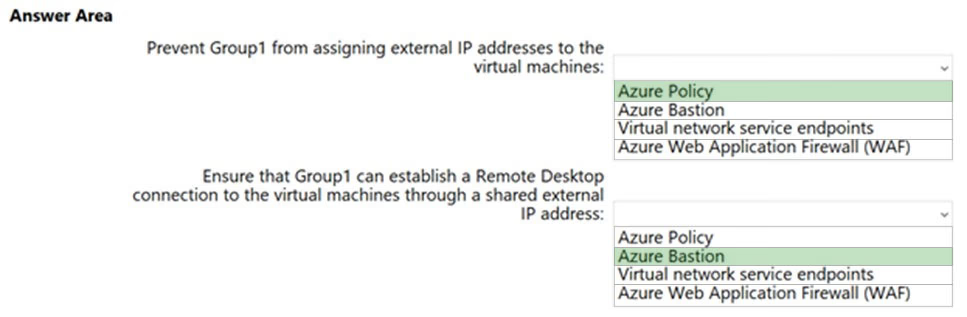
Box 1: Azure Policy -
There is a built-in policy in the Azure Policy service that allows you to block public IPs on all NICs of a VM.
Note: Azure Policy is a powerful tool in your Azure toolbox. It allows you to enforce specific governance principals you want to see implemented in your environment. Some key examples of what Azure Policy allows you to do is:
Automatically tag resources -

✑ Block VMs from having a public IP
✑ Enforce specific regions
✑ Enforce VM size
Box 2: Azure Bastion -
Azure Bastion is a fully managed PaaS service that provides secure and seamless RDP and SSH access to your virtual machines directly through the Azure
Portal.
Azure Bastion is provisioned directly in your Virtual Network (VNet) and supports all VMs in your Virtual Network (VNet) using SSL without any exposure through public IP addresses.
Incorrect Answers:
Virtual Network (VNet) service endpoint provides secure and direct connectivity to Azure services over an optimized route over the Azure backbone network.
Endpoints allow you to secure your critical Azure service resources to only your virtual networks. Service Endpoints enables private IP addresses in the VNet to reach the endpoint of an Azure service without needing a public IP address on the VNet.
Reference:
https://blog.nillsf.com/index.php/2019/11/02/using-azure-policy-to-deny-public-ips-on-specific-vnets/ https://azure.microsoft.com/en-us/services/azure-bastion/