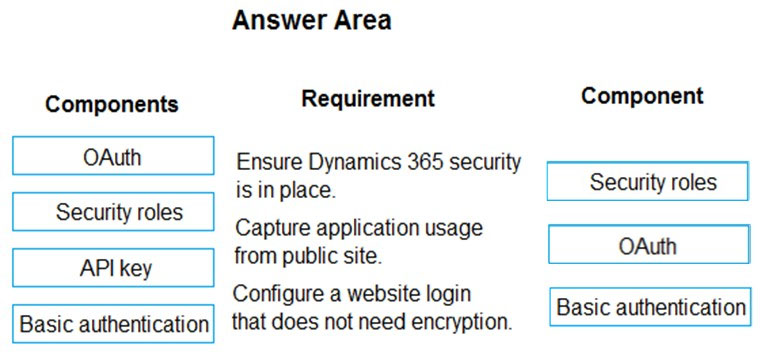
Box 1: Security roles -
A security role defines how different users, such as salespeople, access different types of records. To control access to data, you can modify existing security roles, create new security roles, or change which security roles are assigned to each user. Each user can have multiple security roles.
Security role privileges are cumulative: having more than one security role gives a user every privilege available in every role.
Each security role consists of record-level privileges and task-based privileges.
Box 2: OAuth -
Oauth 2.0 is the most frequently used type, which uses the Oauth 2 authentication framework to authenticate with the service. Before using this authentication type, you'll need to register your application with the service so that it can receive access tokens for the users.
For example, Register the application in Azure AD shows how to register an application with the Azure Active Directory service.
During the connection creation process, the user will be asked to enter the credentials for login to the service. These credentials will be used by the application to get an authorization token. For every request, this authorization token will be sent to your service through the Authorization header.
Box 3: Basic Authentication -
Basic Authentication is the simplest type of authentication, where the user just has to provide the username and password to create the connection.
Note: Before using any connector in Azure Logic Apps, Microsoft Power Automate, or Microsoft Power Apps, the user needs to create a connection by authenticating to the backend service.
Authentication types -
The different types of authentication that are currently supported are:
No authentication -
Basic authentication -
Api Key based authentication -
Oauth 2.0 -
Reference:
https://docs.microsoft.com/en-us/dynamics365/customerengagement/on-premises/admin/security-roles-privileges https://docs.microsoft.com/en-us/connectors/custom-connectors/connection-parameters