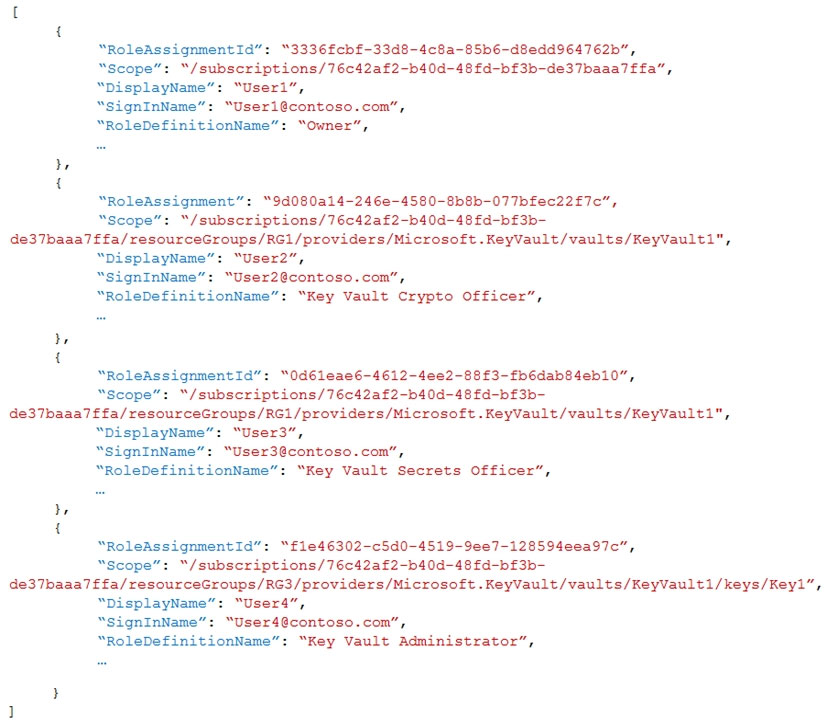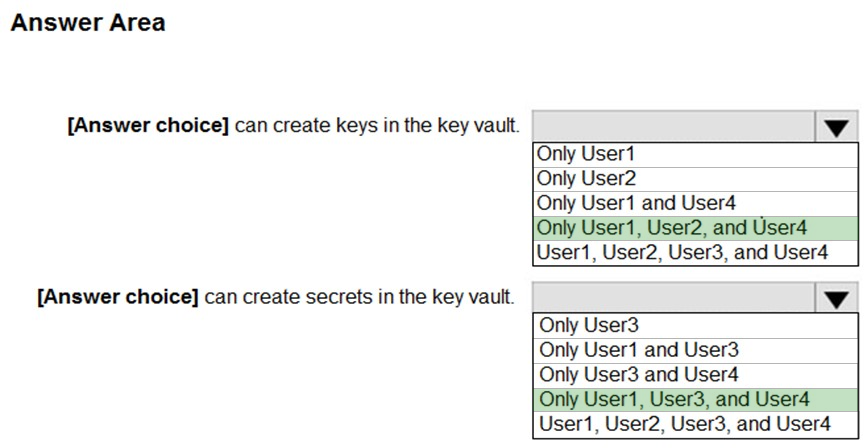
Box 1: Only User1, User 2, and User4
* Owner (User1) - Has full access to all resources including the right to delegate access to others.
* Key Vault Crypto Officer (User2)
Perform any action on the keys of a key vault, except manage permissions.
* Key Vault Administrator (User 4)
Perform all data plane operations on a key vault and all objects in it, including certificates, keys, and secrets
Box 2: Only User1, User3, and User 4
* Key Vault Secrets Officer (User 3)
Perform any action on the secrets of a key vault, except manage permissions. Only works for key vaults that use the 'Azure role-based access control' permission model.
Reference:
https://docs.microsoft.com/en-us/azure/key-vault/general/rbac-guide