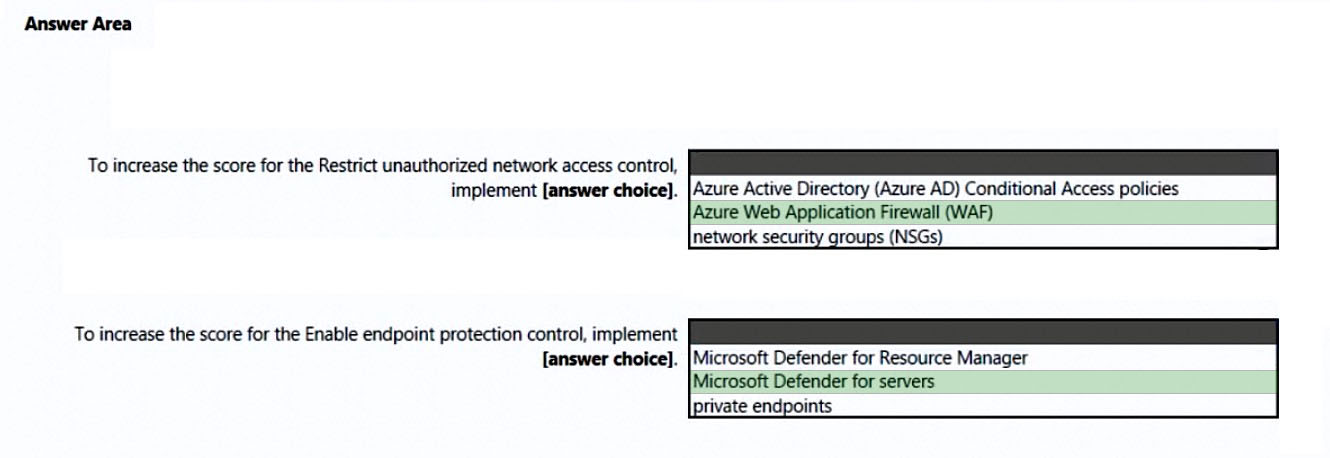
Box 1: Azure Web Application Firewall (WAF)
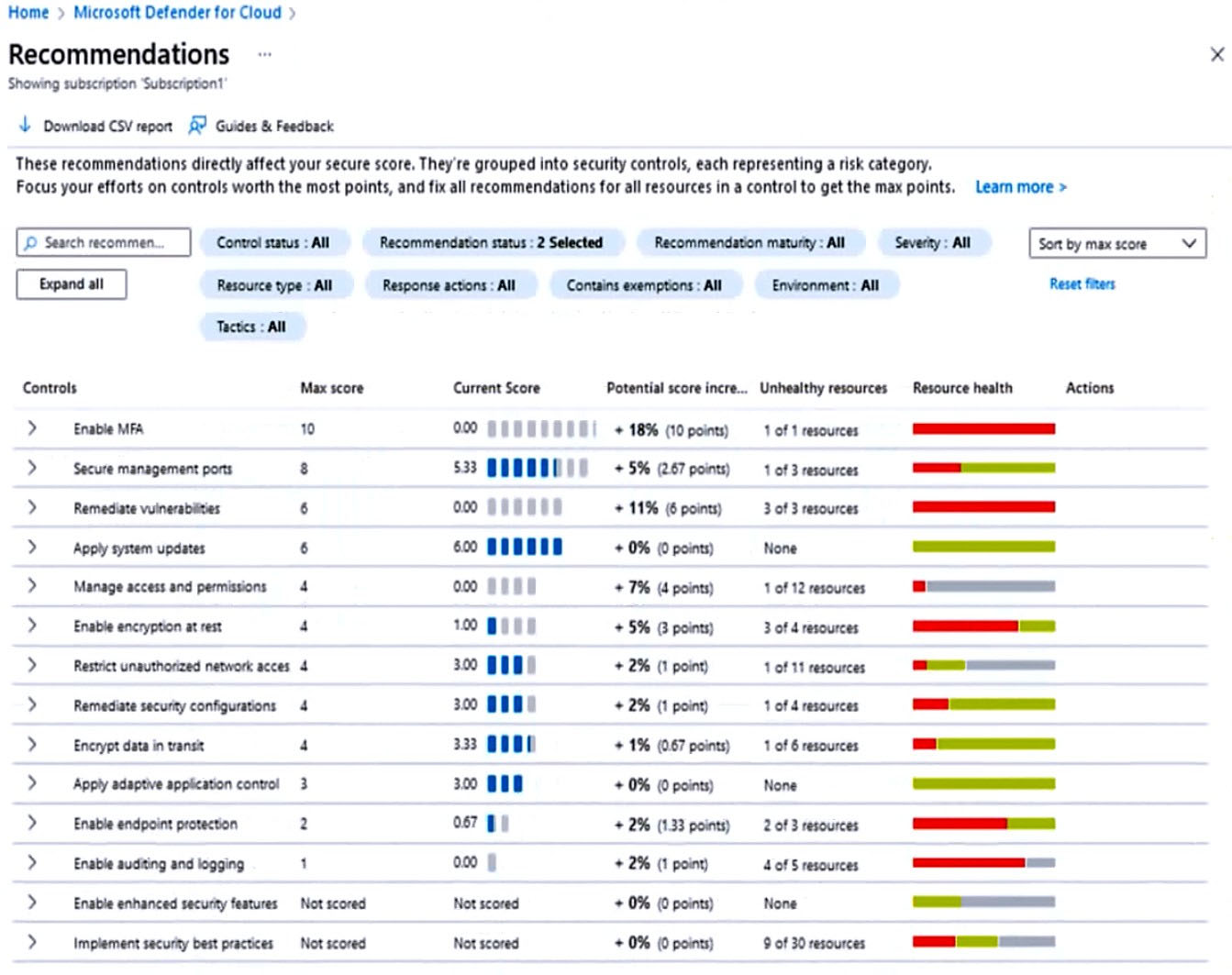
Restrict unauthorized network access control: 1 resource out of 11 needs to be addresses.
Restrict unauthorized network access - Azure offers a suite of tools designed to ensure accesses across your network meet the highest security standards.
Use these recommendations to manage Defender for Cloud's adaptive network hardening settings, ensure you've configured Azure Private Link for all relevant
PaaS services, enable Azure Firewall on your virtual networks, and more.
Note: Azure Web Application Firewall (WAF) is an optional addition to Azure Application Gateway.
Azure WAF protects inbound traffic to the web workloads, and the Azure Firewall inspects inbound traffic for the other applications. The Azure Firewall will cover outbound flows from both workload types.
Incorrect:
Not network security groups (NSGs).
Box 2: Microsoft Defender for servers
Enable endpoint protection - Defender for Cloud checks your organization's endpoints for active threat detection and response solutions such as Microsoft
Defender for Endpoint or any of the major solutions shown in this list.
When an Endpoint Detection and Response (EDR) solution isn't found, you can use these recommendations to deploy Microsoft Defender for Endpoint (included as part of Microsoft Defender for servers).
Incorrect:
Not Microsoft Defender for Resource Manager:
Microsoft Defender for Resource Manager does not handle endpoint protection.
Microsoft Defender for Resource Manager automatically monitors the resource management operations in your organization, whether they're performed through the Azure portal, Azure REST APIs, Azure CLI, or other Azure programmatic clients. Defender for Cloud runs advanced security analytics to detect threats and alerts you about suspicious activity.
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/secure-score-security-controls