HOTSPOT
-
You have a Microsoft 365 E5 subscription.
The subscription contains users that have devices onboarded to Microsoft Defender for Endpoint. Defender for Endpoint is configured to forward signals to Microsoft Defender for Cloud Apps.
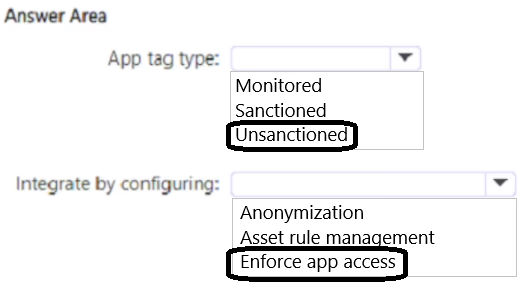
Cloud Discovery identifies a risky web app named App1.
You need to block users from connecting to Appl from Microsoft Edge. Users must be able to bypass the restriction.
Which type of app tag should you use. and what should you configure to integrate Defender for Endpoint with Defender for Cloud Apps? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.