HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
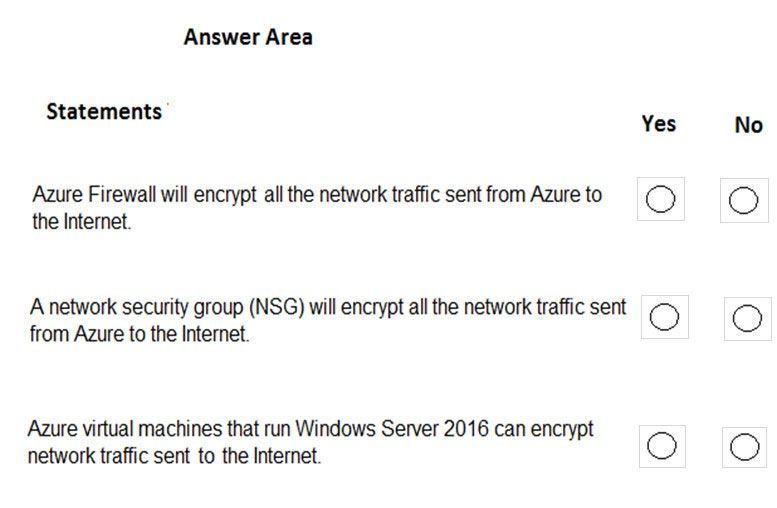
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:


Box 1: No -
Azure firewall does not encrypt network traffic. It is used to block or allow traffic based on source/destination IP address, source/destination ports and protocol.
Box 2: No -
A network security group does not encrypt network traffic. It works in a similar way to a firewall in that it is used to block or allow traffic based on source/ destination IP address, source/destination ports and protocol.
Box 3: No -
The question is rather vague as it would depend on the configuration of the host on the Internet. Windows Server does come with a VPN client and it also supports other encryption methods such IPSec encryption or SSL/TLS so it could encrypt the traffic if the Internet host was configured to require or accept the encryption.
However, the VM could not encrypt the traffic to an Internet host that is not configured to require the encryption.
Reference:
https://docs.microsoft.com/en-us/azure/security/azure-security-data-encryption-best-practices#protect-data-in-transit
I think last answer is YES: Windows 2016 can encrypt data
Ok, but could you please mention the feature or technique which Win16 uses to encrypt network traffic ?
Transport Layer Securtiy (TLS)
thats only part of VPN
Any (modern) web server installed on a Windows server 2016 could use TLS (or HTTPS bindings) - because that's how a good web server should be (and a common feature too).
SMB 3.x
SSL and TLS, SFTP. Windows can't just start offloading data arbitrarily. There needs to be a defined set of processes and procedure to do that. In which case you as the admin makes the decision.
By default, any Windows doesn't encrypt outgoing/incoming traffic unless there a VPN setup. So answer is correct "No"
Windows CAN encrypt data, which is all that is being asked for. In matters like this where the correct answer is ambiguous, I'm inclined to go with the one that makes Microsoft look good.
You don't need a VPN to encrypt traffic. Install an SQL Server and configure TLS connections and you have encrypted traffic. Install an IIS web server (in windows features, anyone can have it) and configure HTTPS bindings and you have encrypted traffic. You can also deny HTTP traffic in IIS and allow only the HTTPS encrypted connections.
Yes captain obvious. Keyword is by default, it doesnt do that.
Umm actually, by default it does send data encrypted to the internet. What is going to be one of the first things you do when you stand up a VM? Go to the internet. Let's say you stood up the VM and decided to upload files to OneDrive using a browser. What protocol is that browser going to leverage? That's right SSL with some form of TLS encrypting the data. This should be yes.
You are correct except question is "Can encrypt data SENT to internet", so question is only about outbound data.
Box 3 is also "NO". You cannot encrypt ALL kind of traffic from Azure VMs sent to the Internet! You can only encrypt traffic between two TRUSTED endpoints. Obviously the Internet isn't the trusted endpoint. In order to make it work, the use of a VPN gateway is required, and then the traffic can be encrypted "over" the public connection - Internet, between Azure VMs/vNets and the trusted on-premises locations. "You can use an Azure VPN gateway to send encrypted traffic between your virtual network and your on-premises location across a public connection, or to send traffic between virtual networks." References: https://docs.microsoft.com/en-us/azure/security/fundamentals/encryption-overview
There is no VPN gateway required. This is simply asking about enrypting network traffic which pretty much every webserver in existance is able to do, whether its based on the internet or internal network communications. The two endpoints don't necessarily have to trust each other. Its usually one-sided unless with the server needing to prove its trustworthy, unless there is client cert authentication too. All that needs to happen is that a server presents a public cert on the initial client connection and the client decides whether or not to trust the server during the TLS handshake. This depends on details on the cert such as the CA and available ciphers they agree upon. Once the TLS handshake is completed and both sides have the the symmetric keys then the server begins encrypting data and sending it out over the network for the client to decrypt and vice versa. Can an azure VM that runs windows server 2016 encrypt network traffic? The answer is definitely Yes, or microsoft would be going quickly out of business.
Definitely this is the 2nd most BS question from Microsoft after that Powershell in CLI question
I agree.
No, No, No. Firewall, NSG, and Windows do not encrypt the network traffic. Just do filtering.
first 2 questions say "will" which they won't. The 3rd one for Windows 2016 says "can" and 2016 can encrypt
NO NO YES - Azure virtual machines that run Windows Server 2016 ***can*** encrypt the network traffic sent from the virtual machies to a host on the Internet. Notice "can", given that Windows Server 2016 can be configured to do so
This one would be all three NO but beware, only situation when it would be true if VPN is involved.
Statement poor in information, it seems "prank" but every modern OS has TLS support. NNY
3 is a Yes. Firewall and NSG do not encrypt. Server 2016 does.
Any Windows NT since V.4 can encrypt data using IPSec tunnel, why third choice is NO ?
Got this from: https://pupuweb.com/microsoft-azure-fundamentals-az900-actual-exam-question-answer-dumps-3/2/ The Question (213) was: Azure virtual machines that run Windows Server 2016 can encrypt the network traffic sent from the virtual machies to a host on the Internet. Answer: No The question is rather vague as it would depend on the configuration of the host on the Internet. Windows Server does come with a VPN client and it also supports other encryption methods such IPSec encryption or SSL/TLS so it could encrypt the traffic if the Internet host was configured to require or accept the encryption. However, the VM could not encrypt the traffic to an Internet host that is not configured to require the encryption.
No. Azure Firewall does not encrypt network traffic, it provides network-level protection by filtering inbound and outbound traffic based on rules. No. A Network Security Group (NSG) also does not encrypt network traffic. It simply controls access by permitting or denying network traffic to resources connected to Azure Virtual Networks (VNet). Yes. Azure VMs that run Windows Server 2016 can encrypt network traffic sent to the internet, but this would be dependent on the application or service running on the VM implementing encryption, such as using HTTPS for web traffic. It's not a feature of the VM or the operating system itself.
hellooooooooooooooooo
No, No, Yes
According to https://azure.microsoft.com/en-us/products/azure-firewall/ it says , Azure Firewall decrypts outbound traffic, performs required security checks, and then encrypts the traffic to the destination. It means that Azure Firewall does encryption for outbound traffic.
No Azure Firewall doesn't encrypt or decrypt traffic inbound or outbound. If you are sending a traffic with HTTPS, how will Firewall know what is the destination as the hostname headers are encrypted. So it just decap the packet to find the Hostheader and then check that against the network and application rule and allow/deny the request. see - https://learn.microsoft.com/en-us/answers/questions/1141553/does-azure-firewall-encrypt-all-the-network-traffi
Answer is NNY
https://learn.microsoft.com/en-us/azure/security/fundamentals/encryption-overview#in-transit-encryption-in-azure-virtual-machines By using SMB 3.0 in VMs that are running Windows Server 2012 or later, you can make data transfers secure by encrypting data in transit over Azure Virtual Networks. By encrypting data, you help protect against tampering and eavesdropping attacks. Because of this, I think 3 should be YES
n n yyyyyyyy
y using SMB 3.0 in VMs that are running Windows Server 2012 or later, you can make data transfers secure by encrypting data in transit over Azure Virtual Networks. By encrypting data, you help protect against tampering and eavesdropping attacks. Administrators can enable SMB encryption for the entire server, or just specific shares. Is it not applicable here, because of windows version is not mentioed?