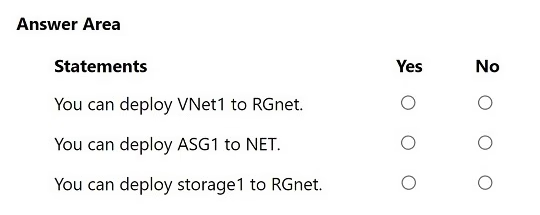
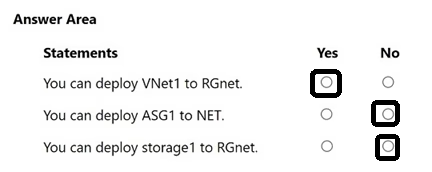
HOTSPOT
-
You have an Azure subscription named Sub1 that contains two resource groups named RGnet and NET.
You have the Azure Policy definition shown in the following exhibit.

You assign the policy definition to Sub1 and NET.
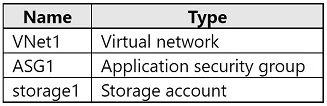
You plan to deploy the resources shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.