Refer to the exhibits:
Exhibit 1 -
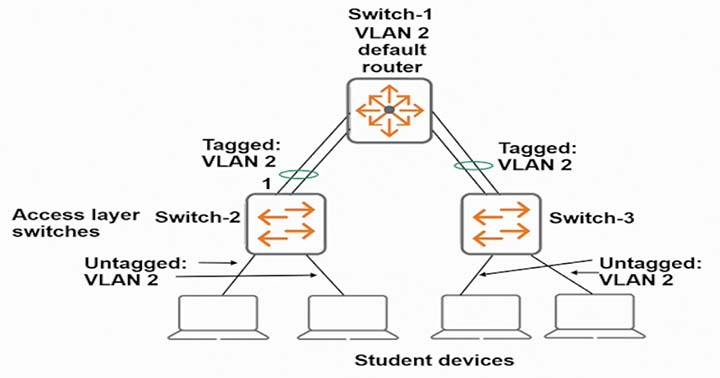
Exhibit 2 -
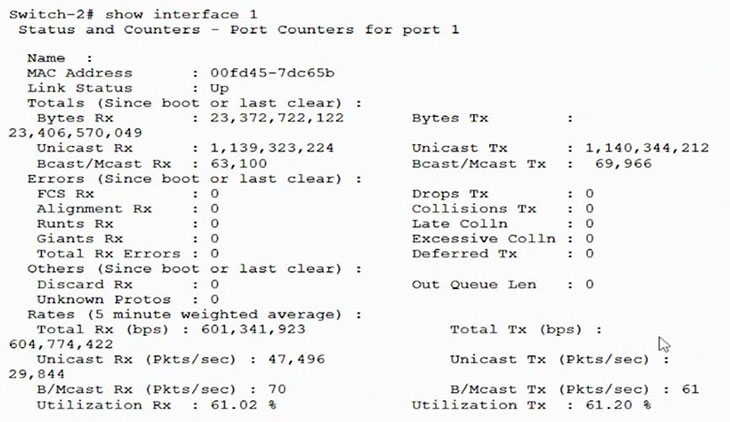
A network administrator at a university notices high utilization on links between the access layer and core. The output shown in the exhibit is characteristic of samples taken several times an hour during congestion. The administrator suspects file sharing and other unauthorized traffic, and decides to use an ACL to permit only HTTP, HTTPS, and a few other authorized types of traffic.
How can the administrator apply the ACL to address both the security and the congestion problem?