Examine the following AOS-CX switch configuration:
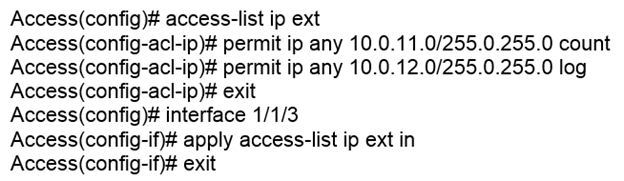
Which statement correctly describes what is allowed for traffic entering interface 1/1/3?
Examine the following AOS-CX switch configuration:

Which statement correctly describes what is allowed for traffic entering interface 1/1/3?
The access control list (ACL) configuration 'permit ip any 10.0.11.0/255.0.255.0 count' and 'permit ip any 10.0.12.0/255.0.255.0 log' means that any IP traffic is allowed to 10.0.11.0/24 and 10.0.12.0/24. The first line will count the packets to 10.0.11.0/24 and the second line will log the packets to 10.0.12.0/24. However, the option 'Traffic from 10.0.12.0/24 will generate a log record when accessing 10.0.11.0/24' conflicts with the configuration since it is concerned with traffic directed to 10.0.12.0/24 and not originating from it. Therefore, the correct interpretation is that 'IP traffic from 10.0.11.0/24 is allowed to access 10.1.12.0/24', which makes option B the correct answer.
The question is " Which statement correctly describes what is allowed for traffic entering interface 1/1/3?" I think that what is allowed to enter the interface 1/1/3 is everything from: ANY TO -> 10.X.11.X(this is allowed and counted) or 10.X.12.X(this allowed and loged), thats why i think the answer is B Everything with other "destination" should be denny.
I agree , B
I think it's C. ACL entries work with wildcard mask. The wildcard mask is 255.0.255.0. This is a wildcard mask and not a subnet mask also because it is not a valid subnet mask. In a wildcard mask made in this way you have to match bits where wildcard is 0. So, it matches packets where the DESTINATION IP ADDRESS is X.0.X.0. In a /24 network, you will never have a destination IP where the last octet is 0. So i think this ACL is not valid, by the way, the only answer that matches the ACL entries is the C BUT it matches the first entry, so it will never generate a log, but a counter increment. This is a bad question with no matching answers. The "best matching" answer is C even if it is wrong.
Got it backwards. 10.0.12.0/255.0.255.0 will match 10.1.12.0/24 .Therefore B should be correct. Right from the student guide. 1's match 0's ignore. Ch. 5 - Task 2 , or search book for 255.0.255.0 "In this example any destination IP address that has '10' in the first byte, and '12' in the third byte will match the rule.
In the official HPE study book, it clearly states that AOS-CX switches do not support Wildcard Masks when creating ACEs.
As per ACL definition: Matching seq 20 "permit ip any 10.0.12.0/255.0.255.0 log" So trafic from any source ip address is permitted to 10.x.12.x
It's possible that B is correct but look at the log and count entries in the commands. I think C is correct. A log entry will be generated for this subnet.
the log count is only active for destination 10.x.12.x
Only log*
AOS-CX does not support Wildcard / Inverted Subnet Masks... Study Guide states: "AOS-CX switches do not support wildcard masks - only prefixes or subnet masks - when creating ACEs". Therefore C is most probably the answer
I think answer is B.
People seem to be confused by inverted mask/wildcard masks. They would be correct for Cisco switches, but AOS-CX does NOT use wildcard masks; "AOX-CX switches do not support wildcard masks - only prefixes or subnet masks - when created ACEs." Cisco: 255.0.255.0 = xx.123.xx.123 AOS-CX: 255.0.255.0 = 123.xx.123.xx My answer is B.
but 10.1.12.0 is not matching the wild card mask. i see answer C more accurate, because count will generate syslog message right ?
sorry it is subnet mask no wild card, B is correct
B sound correct but check the ip addresses properly 10.0.11.0/24 and 10.0.12.0/24 where is 10.1.12.0/24 coming from? C is correct then
My opinion: B Only traffic destined TO the listed subs is allowed This excluded A and D Only traffic TO 10.1.12.0 is logged This excludes C This leaves B .11.0 is part of ANY so it is allowed to access .12.0 This traffic will be logged but that isn't part of the answer.
I think the answer is D. Here is the simplified access list with X=any (0-255) permit any -> X.0.X.0 count permit any -> X.0.X.0 log They are practically the same ACL with only different the top does count and bottom does log. A. IP traffic from 10.1.11.0/24 is allowed to access 10.1.110.0/24 We dont care with source (10.1.11.0/24). The source can be any. But the destination is 10.1.110.0/24 and it does not match. The second octet must be 0. B. IP traffic from 10.0.11.0/24 is allowed to access 10.1.12.0/24 Same with A. 10.1.12.0 does not match because second octet is 1 C. Traffic from 10.0.12.0/24 will generate a log record when accessing 10.0.11.0/24 This actually match both ACEs but since ACL matches from top to bottom, so it will match the top ACE (count). D. IP traffic from 10.1.12.0/24 is allowed to access 172.0.1.0/23 this would match the ACL. We dont care about source and destination 172.0.1.0 (match X.0.X.0) Samw
B is correct
No wildcard mask with Aruba CX. B answer
B is correct
B is correct
B is correct
B is correct