An attacker compromises a host and runs the following commands. What did the attacker do?
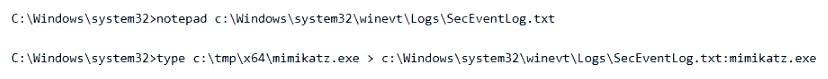
An attacker compromises a host and runs the following commands. What did the attacker do?

An attacker did not directly edit a log file based on the provided commands. Instead, they used Alternate Data Streams (ADS) to hide a file, specifically by appending mimikatz.exe to the SecEventLog.txt file. This is a common technique to obscure a malicious executable by hiding it within a seemingly innocent file.
The answer should be "C" as it is an example of using Alternate Datastreams for hiding files.