Refer to the exhibit, which shows a non-protected OT environment.
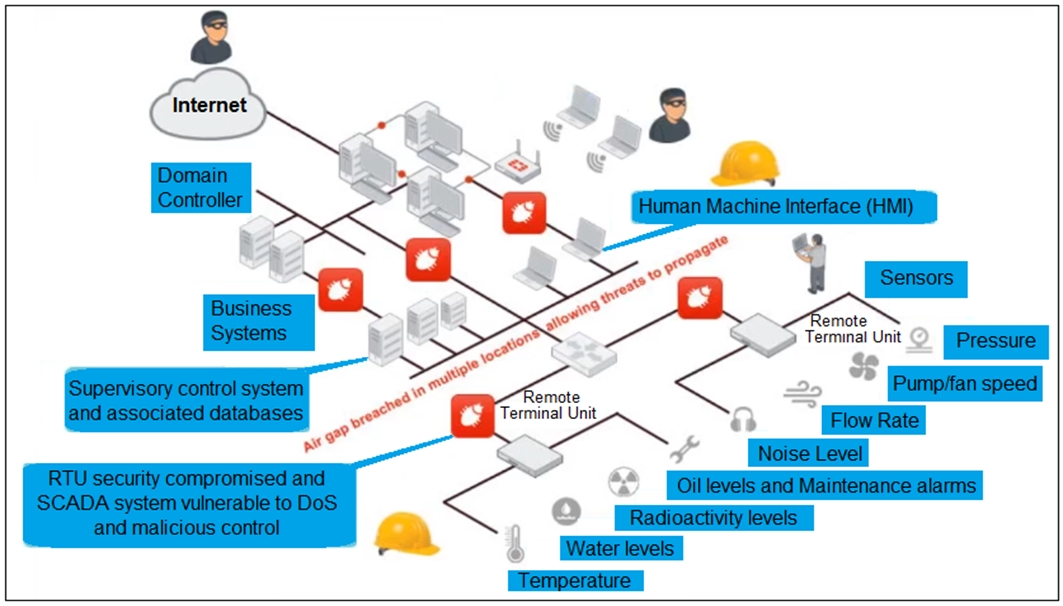
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
Refer to the exhibit, which shows a non-protected OT environment.

An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
To protect the OT network, the administrator should implement the following steps. First, deploy a FortiGate device within each ICS network to provide localized security controls and offer protection from threats that propagate within each network. Second, configure firewall policies with industrial protocol sensors to monitor and filter traffic specific to industrial protocols, thereby protecting against threats targeting these protocols. Finally, use segmentation to divide the network into smaller segments, which helps to contain and prevent the spread of threats and makes the network easier to manage and secure.
BDE for sure
This should be B, D, E from study guide, page 181
study guide OT 6.4 , page 181
Explanation/Reference:studyguide_page181
Ans: BDE
To protect the different IS environments and limit the propagation of attacks coming from IT to the different ICS networks or elements, segmentation is recommended. In this example, the FortiGate creates conduits that stop threats from propagating between ICS network 1 and ICS network 2. Expanding on this concept, by placing FortiGate devices at strategic points within the IS network itself, you can granularly segment different zones creating an extra layer of protection for the endpoints and controllers as well as protect the data flow and communications between them. FortiGate has specific ICS and SCADA-aware functionality, and can identify and police most of the common ICS and SCADA protocols. In parallel to this specific protocol support, additional vulnerability protection is provided for applications and devices from the major ICS manufacturers through a set of signatures.
The correct answers are C, D, and E. A, B, and C are incorrect answers. A. Powering on the VM will not allow it to be live migrated to Clusters A and B. B. Disabling EVC will prevent the VM from being live migrated to Clusters A and B. C. Rebooting the VM will not allow it to be live migrated to Clusters A and B.