Refer to the exhibit.
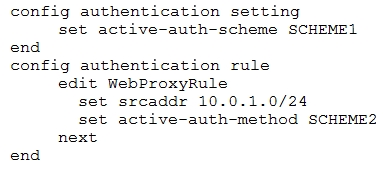
The exhibit shows a FortiGate configuration.
How does FortiGate handle web proxy traffic coming from the IP address 10.2.1.200, that requires authorization?
Refer to the exhibit.

The exhibit shows a FortiGate configuration.
How does FortiGate handle web proxy traffic coming from the IP address 10.2.1.200, that requires authorization?
FortiGate handles web proxy traffic based on authentication schemes. The configuration shows an active authentication scheme set to SCHEME1 and an authentication rule for traffic from 10.0.1.0/24 using SCHEME2. Since the IP address 10.2.1.200 does not fall within the 10.0.1.0/24 subnet, it is not affected by the specific rule for SCHEME2. Therefore, the traffic from 10.2.1.200 will be handled using the general active authentication scheme, which is SCHEME1.
D is correct
d es correcto
The answer is D.
- FGT Security 7.2 p310 - The application control profile scans for matches in this order: ○ Application and filter overrides: If you have configured any applications overrides or filter overrides, the application control profile considers those first. It looks for a matching override starting at the top of the list, like firewall policies. ○ Categories: Finally, the application control profiles applies the action that you've configured for applications in your selected categories.