You need to recover an account localadmin02 for target server 10.0.123.73 stored in Safe Team1.
What do you need to recover and decrypt the object? (Choose three.)
You need to recover an account localadmin02 for target server 10.0.123.73 stored in Safe Team1.
What do you need to recover and decrypt the object? (Choose three.)
ADE
Reference:
https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/Server-Keys.htm?TocPath=Administration%7CComponents%
7CDigital%20Vault%7CAdvanced%20Digital%20Vault%20Environment%7CCyberArk%20Vault%20Structure%7C_____3
https://cyberark-customers.force.com/s/article/How-to-recover-password-using-recover-exe-outside-of-Vault
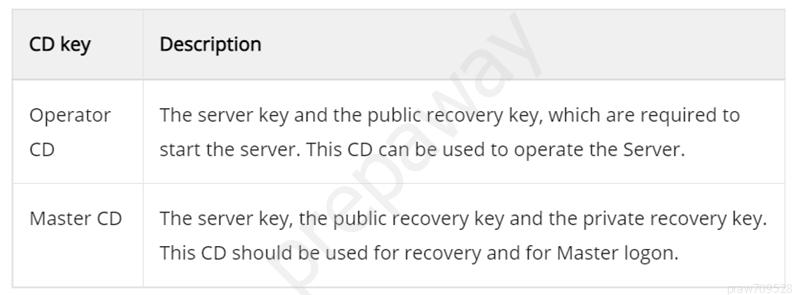
Should be ADE The public recovery key enables the recovery option in the Safe. This enables the Safe to be opened with the private recovery key. The public recovery key is usually stored with the server key and the path to the key is defined in the DBParm.ini file. https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/Server-Keys.htm?tocpath=Administrator%7CComponents%7CDigital%20Vault%7CAdvanced%20Digital%20Vault%20Environment%7CCyberArk%20Vault%20Structure%7C_____3
Have tested in my lab C:\Program Files (x86)\PrivateArk\Server>Recover.exe Enter file to recover (wildcards are accepted): C:\PrivateArk\Safes\Data\Del\Root\*.* Enter output directory for recovered files: C:\Recover Enter private recovery key directory: C:\Users\Administrator\Downloads\DemoMasterKeys_2 Verify Recovery Private key is in C:\Users\Administrator\Downloads\DemoMasterKeys_2, and press any key Recovering file Operating System-CyberArk-WindowsDomainAccounts-192.168.10.#000000000000001#.66-administrator into C:\Recover\Operating System-CyberArk-WindowsDomainAccounts-192.168.10.#000000000000001#.66-administrator 1 file recovered successfully. C:\Program Files (x86)\PrivateArk\Server>
and preivous 120 answer is correct?