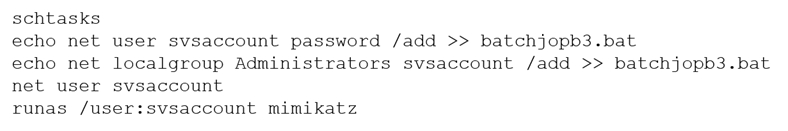
A penetration tester ran the following commands on a Windows server:
Which of the following should the tester do AFTER delivering the final report?
A penetration tester ran the following commands on a Windows server:

Which of the following should the tester do AFTER delivering the final report?
Once the penetration test is complete, it is crucial to remove any accounts or credentials that were created during the test to prevent unauthorized access and ensure the system's security. The commands used indicate that the tester created a new user account (svsaccount) and added it to the Administrators group, which could pose a significant security risk if left in place. Therefore, after delivering the final report, the tester should remove the tester-created credentials to revert the system to its original state and maintain its integrity.
D. Remove the tester-created credentials. The tester has created a new user account (svsaccount) and set the password to "password", and then added the user account to the local Administrators group. The tester also ran mimikatz, which is a tool that allows the tester to obtain clear text password, hashes, and other sensitive information. After delivering the final report, the tester should remove the tester-created credentials by running the following command: "net user svsaccount /delete". This will remove the tester-created user account and its associated credentials. Deleting the scheduled batch job (Option A) is not necessary as the tester-created account has been removed. Closing the reverse shell connection (Option B) would be useful if the tester had created one, but it is not mentioned in the given information. Downgrading the svsaccount permissions (Option C) is not necessary as the account has been removed.
This is a tricky one. A & D are part of the cleanup. I may be confusing myself, but the initial commands are only to append the commands to the .bat file, not execution the commands. I feel it's A as it will continue to create the svsaccount even after you delete it.
deleting the scheduled batch job (option A) should be prioritized as it directly prevents the execution of potentially harmful commands contained within the batch file. For example, if commands in the batch file are used to create the svsaccount, and elevate permissions, as some have said here. EVEN IF step 1 is: delete the svsaccount, and/or downgrade the permissions AND step 2 is: delete the batch file THEN the batch file could possibly run between step 1 and step 2, effectively recreating the account that was just deleted SO delete the batch file first
a couple of these seen reasonable answers I guess the difference between right and wrong is 'AFTER delivering the final report?'. Does anyone have an idea if any of these are done BEFORE the report as a rule of thumb? I'm pretty sure closing the shell session would be
The commands executed by the penetration tester include the creation of a batch job using the "Schtasks" command, which schedules the execution of the "batchjob3.bat" file. It is important to remove or delete any artifacts or traces left behind during the penetration testing engagement.
D is correct answer
The command "echo net user svsaccount password /add >> batchjopb3.bat" adds the command "net user svsaccount password /add" to the file "batchjopb3.bat". This command is used to create a new user account with the username "svsaccount" and password "password" on a Windows system. The command "runas /user:svsaccount mimikatz" is used to execute the program "mimikatz" with the credentials of the user "svsaccount". This could be used to gain access to sensitive data stored in the system or to exploit vulnerable services on the system.
D is the answer for sure
D is correct
After delivering the final report, the tester should: D. Remove the tester-created credentials. Explanation: • The steps outlined in the command sequence indicate that new user accounts (susaccount and svsaccount) were created and added to the Administrators group. These accounts are likely used for maintaining access and performing tasks during the penetration test. • It is critical to remove these tester-created credentials to ensure that no unauthorized accounts are left on the client’s system, which could pose a security risk.
He should restore anything as it was before. Therefore I would go with D. But why not A: The commands don't show that he created the scheduled batch job. The first line "schtasks" just lists all scheduled tasks. It does not create a new one. So you have to assume that line 2 and 3 just add the commands to an existing task he found in the listing. But certainly he does not create a new one. Deleting it probably deletes also something that was already there on purpose and should remain. So instead of deleting it he should only remove the commands from the bat file he added or recover the original file, but these are no an answer options.. Why not B: The commands the question references have nothing to do with reverse shell Why not C: Line 4 and 5 let assume that the svsaccount exists. If the account would have existed before, he would not have to have it added to the batch job file (line 2). And only would require the administrator permissions to be added (line 3). Downgrade would only be correct if the account existed already. This leaves answer D as the only option.
The Question is "after the Report". Schtasks should be deleted before the final report. The svsaccount ist to proof the report.
Wow this is really cool. As I understand, the pentester used an existing .bat file to create a new admin user and use it to run mimikatz. Tester can't delete the schtasks .bat -- although cleanup requires to restore the original script so it don't keep creating the same user.
I'll go with C. service accounts have elevated permissions, test accounts do not.
As masso stated, the scheduled job is what is creating the account. The pentester didn't create this manually. So if the sched task runs again after the account was deleted, the account and action done by the sched task will recreate the user and run the exploit all over again. So deleting or downgrading access will just be redone/made on next scheduled task. Than answer must be A
D. Remove the tester-created credentials. Based on the commands, the penetration tester created a new user account "svsaccount" with a password and added it to the Administrators group. They then used those credentials to run mimikatz for further access. After the test is complete and findings delivered, the tester should remove any accounts, files, tools etc. that they created or brought in. This includes deleting the "svsaccount" user to restore the system to its original state. Deleting scheduled jobs, closing connections, or downgrading permissions may be applicable in other scenarios, but are not specifically indicated in this example. The priority should be removing anything the tester added.
The series of commands described in the question shows that the penetration tester has created a new user account (svsaccount) and added it to the Administrators group on the Windows server. This is part of the penetration test, and it would be inappropriate to leave these changes in place after the test is complete. The responsible action after delivering the final report would be to remove any changes made to the client's environment, including deleting any accounts or credentials created during the test. Leaving these in place could pose a significant security risk. Therefore, the correct answer is: D. Remove the tester-created credentials.
DDDDDDDD