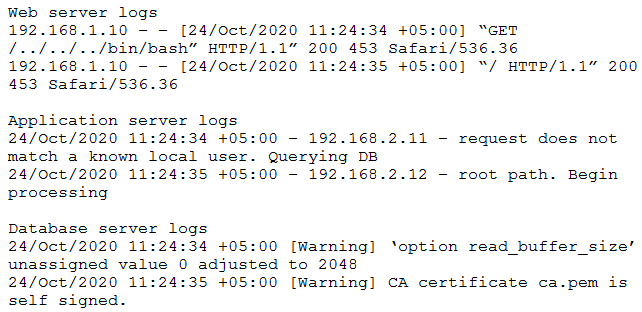
You are correct that storing the value of the $_SERVER['REMOTE_ADDR'] may not always provide the actual IP address of the client, especially if the request was proxied through a load balancer. However, the option E was recommended in this scenario because the web server logs are the only logs that show the IP address of the client, and storing the $_SERVER['REMOTE_ADDR'] value in the web server logs would allow for tracking the source of the incident.
In contrast, enabling the X-Forwarded-For header at the load balancer, as suggested in option A, would provide the actual IP address of the client even if the request was proxied through the load balancer. However, since the load balancer cannot store logs, enabling the X-Forwarded-For header would not be sufficient to ensure future incidents can be traced back to their sources.
Therefore, storing the $_SERVER['REMOTE_ADDR'] value in the web server logs, as suggested in option E, would be the best option to ensure future incidents can be traced back to their sources in this specific scenario.