Given the following log snippet from a web server:
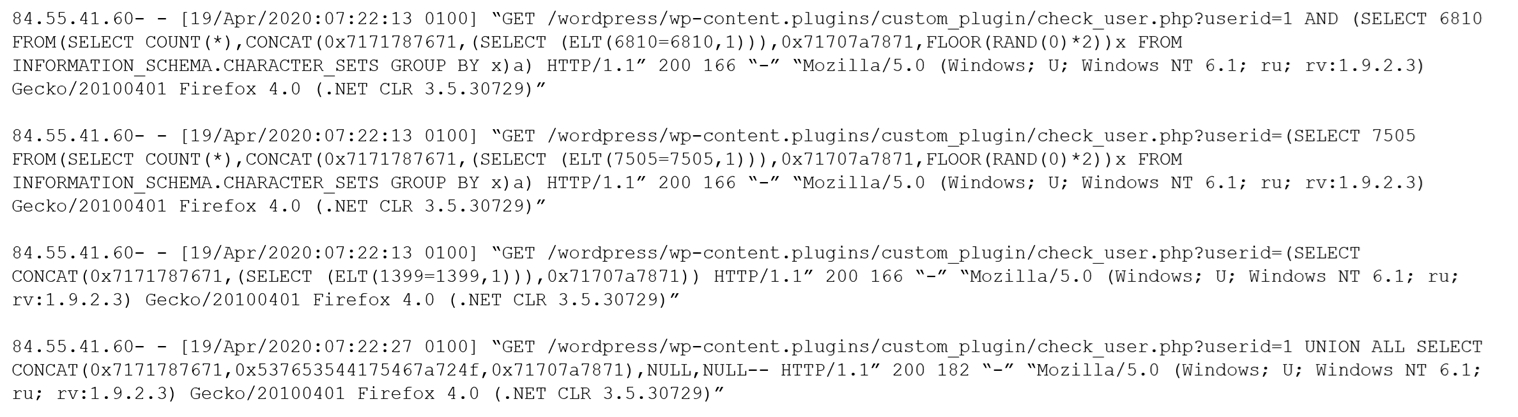
Which of the following BEST describes this type of attack?
Given the following log snippet from a web server:

Which of the following BEST describes this type of attack?
The log snippets show attempts to manipulate SQL queries through the URL parameters in the requests. The use of SQL statements such as SELECT, CONCAT, and UNION ALL SELECT in the userid parameter strongly indicates that this is an SQL injection attack. SQL injection involves inserting or manipulating SQL code in input fields to exploit potential vulnerabilities in the database layer of an application.
I think this is showing a SQL injection.
Keyword schema, deals with database layout. Hence SQL
Clearly shows SQL queries.
Clearly trying to pass SQL code for the user field, this is clearly an example of SQL injection. Cross site forgery is when you try to bypass or change the web path to by pass the index.
Attempted SQL injection into userid
SQL injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id https://www.w3schools.com/sql/sql_injection.asp
It's definitely SQL injection, no doubt
I agree. 'A' seems to be correct.
A is the correct answer "SQL injection"
Source: Verifying each answer against Chat GPT, my experience, other test banks, a written book, and weighing in the discussion from all users to create a 100% accurate guide for myself before I take the exam. (It isn't easy because of the time needed, but it is doing my diligence)
In the given log snippets, the requests to the check_user.php script contain SQL-like statements in the URL parameters such as userid: SELECT statements injected with specific SQL syntax into the userid parameter. Use of UNION ALL SELECT to join maliciously crafted SQL statements. Attempts to perform database operations like SELECT, CONCAT, and UNION. These attempts to manipulate the SQL queries through the URL parameters in the requests suggest an attempt to exploit potential vulnerabilities in the application's database layer, which is characteristic of SQL injection attacks. Therefore, the described attack pattern aligns with option A: SQL injection.
Each log entry shows a request made to the endpoint check_user.php with a parameter userid containing SQL code. The use of keywords like SELECT, FROM, UNION ALL SELECT, and the manipulation of functions and numeric calculations within the parameter value are characteristic of SQL injection attempts