A security analyst discovered that the company's WAF was not properly configured. The main web server was breached, and the following payload was found in one of the malicious requests:

Which of the following would BEST mitigate this vulnerability?
A security analyst discovered that the company's WAF was not properly configured. The main web server was breached, and the following payload was found in one of the malicious requests:

Which of the following would BEST mitigate this vulnerability?
B
Reference:
https://hdivsecurity.com/owasp-xml-external-entities-xxe
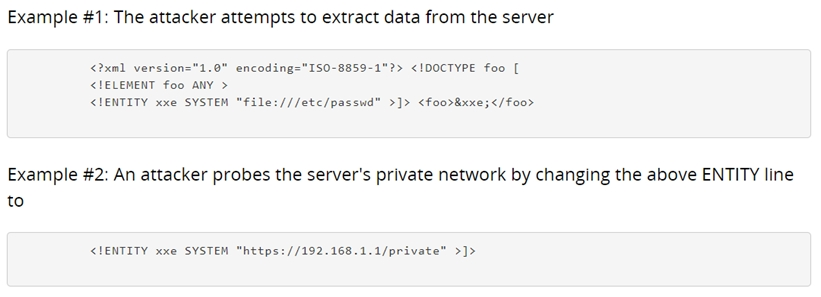
B: seems right An XML External Entity attack is a type of attack against an application that parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser. This attack may lead to the disclosure of confidential data, denial of service, server side request forgery, port scanning from the perspective of the machine where the parser is located, and other system impacts.
The payload in the malicious request indicates the presence of an XML External Entity (XXE) injection vulnerability. This type of vulnerability allows an attacker to read files on the affected system and execute arbitrary code. To mitigate this vulnerability, the company should implement input validation to sanitize user input and prevent the injection of malicious payloads like the one found in the breach. Therefore, the best option is: B. Input validation
WAF is allowing the "input shown" to come through. Input validation keeps payloads out. CAPTCHA is for bots Data encoding would hide the payload. Network intrusion prevention - An excellent option for when a threat actor gets past the WAF, but it's not the BEST for this scenario. Stop the Bleed first, and close the input validation security problem. Source: Verifying each answer against Chat GPT, my experience, other test banks, a written book, and weighing in the discussion from all users to create a 100% accurate guide for myself before I take the exam. (It isn't easy because of the time needed, but it is doing my diligence)
To prevent malicious input from being included in XML documents, validate, and sanitize all user input before including it in an XML document. https://www.indusface.com/blog/how-to-identify-and-mitigate-xxe-vulnerability/
Understanding XXE: The payload provided (<!DOCTYPE doc [ <!ELEMENT doc ANY> <!ENTITY xxe SYSTEM "file:///etc/passwd" > ]><doc>&xxe;</doc>) is designed to exploit an XXE vulnerability by attempting to access the /etc/passwd file. XXE attacks exploit vulnerabilities in XML parsers. Input Validation: Properly validating and sanitizing input data, especially XML content, ensures that harmful payloads are not processed by the application. This includes disabling DTD (Document Type Definition) processing if it's not needed.
The payload provided in the question indicates an XML External Entity (XXE) injection vulnerability. To mitigate this vulnerability, the BEST option is: B. Input validation